All Activity
- Today
-
Josephspeat joined the community
- Yesterday
-
Sergey Diatlov joined the community
-
juan josé Mendinueta joined the community
-
mail joined the community
-
Sergey Nezvankin joined the community
-
Problem with a Wireguard on 5.0.4
Eug Family replied to kopernik15's question in Dev channel issues & test reports
Are static routes registered? Are the allowed IPs correctly specified in the tunnel configuration? Is the firewall enabled for WG? Updated to 5.0.7? -
Gleb Faustov joined the community
- Last week
-

Confirm Button Not Visible in "Install Updates" Screen / 4.3B3
eralde replied to ru.celebi's question in Dev channel issues & test reports
Hello @ru.celebi, which version of the firmware is currently installed on your devices? -

Core::Configurator: not found: "show/sc/mws/wlan"
eralde replied to PriSonerS61's question in Dev channel issues & test reports
Thank you for the report. This will be fixed in one of the future draft versions. The web UI relies on new parts of the API that are not yet publicly available. The error messages will go away, once the API is updated. -

Core::Configurator: not found: "show/sc/mws/wlan"
PriSonerS61 replied to PriSonerS61's question in Dev channel issues & test reports
@Anna_ -
PriSonerS61 started following Core::Configurator: not found: "show/sc/mws/wlan"
-
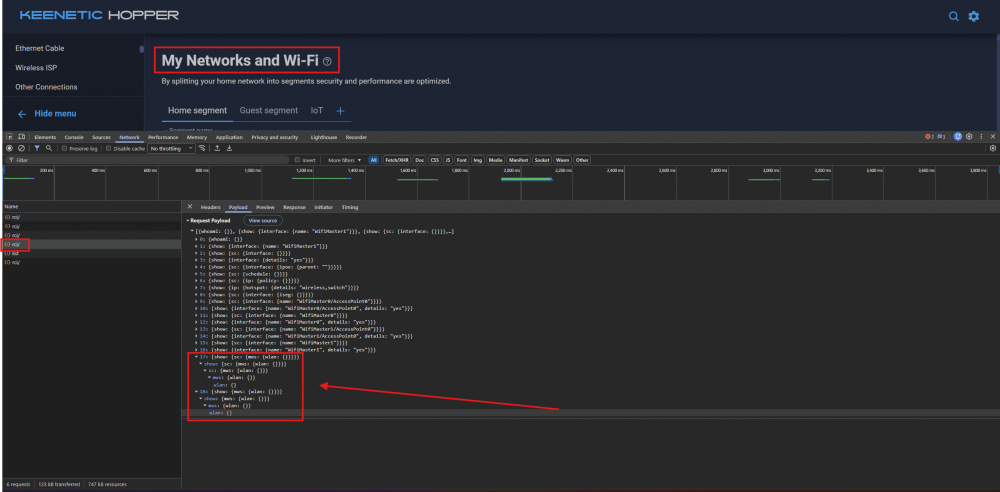
Hello @eralde When accessing the home segment tab, the following error appears in the logs. When checking RCI requests, it appears that such a request actually exists.Tested on versions 5.1 Alpha 4 and 5.1 Alpha 5. The self-test file will be available in the next private message. Core::Configurator: not found: "show/sc/mws/wlan" [http/rci 192.168.1.29] Core::Configurator: not found: "show/mws/wlan" [http/rci 192.168.1.29] https://ibb.co/yngC12Ch
-

Problem with a Wireguard on 5.0.4
Ahmed Ensar replied to kopernik15's question in Dev channel issues & test reports
check ip nat wireguard? interface Wireguard? --> security-level public -
Release 5.1 Alpha 5 Core: fixed return to already installed version when system boots with 'system failed' errors after update (reported by @vasek00) [NDM-4311] DLNA: fixed the service startup operation [NDM-4315] Web: fixed the automatic update of the active connections display (reported by @mega1volt) [NWI-4713] Web: corrected the language set reset upon manual update [NWI-4703] Web: fixed the 'Log in' button on the user authentication page (reported by @Robespierre) [NWI-4718] Web: fixed the tooltip display at the right edge of the Wi-Fi Monitor graph for wider screens (reported by @keenet07) [NWI-4717] Web: corrected the free SMS memory display for certain modem models [NWI-4692] Web: improved the storage status display (reported by @spatiumstas) [NWI-4694] Web: fixed the IP protocol missing in the firewall rule editor (reported by @dimon27254) [NWI-4711] Wireguard: fixed the import of configurations containing ASC parameters (reported by @spatiumstas) [NDM-4313] WSD: confined Hello messages by the Bridge0 interface by default [NDM-4314]
-

After updated Alpha 3…
Ahmed Ensar replied to tulgar's question in Dev channel issues & test reports
Translate: I spent half an hour dealing with recovery, and now I'm back to a clean installation. We were used to the problem-free Alpha, you really surprised everyone with this twist. 😌 -
06/03/2026 Temporary Disabling of Telegram Notifications for Node Reboot Please note that Telegram notifications for the “Node Reboot” event are temporarily disabled due to a technical issue. They will be restored once the problem is resolved. We apologize for any inconvenience caused.
-
No way, sorry. I've never had this problem with other brands, I don't want to write their names here, you can guess. it's not acceptable at all a router gets to defaults for a power outage, thsi is not an hardware failure, it's a corruption of internal settings and for reaction it goes to deafault. It looks that cases happened already, I not the only one, and I'm under shock. Keenetic is not a reliable company to entrust your businness
-
PS5 Connectivity Issues on Titan KN-1812
keen_parish27 replied to Vadym's question in Community Support & Knowledge Exchange
Hi Vadym, Please write to the support team, who will help you investigate the issue. support@keenetic.de -
Captive Portal problem
keen_parish27 replied to ilker Aktuna's question in Community Support & Knowledge Exchange
Good Morning Ilker, We apologize for the delay in responding. That said, this is a forum, not a support platform. Thanks for reporting the issue and the configurations to resolve it. In my previous tests, it was not necessary to explicitly send the “ip nat Chilli0” command, but we have not yet performed tests in an environment similar to yours, with the UAM server in another LAN segment. As for the firewall rule, the behavior is expected. Traffic between different segments is denied by default, so if you need to reach a resource in another segment, you must add a rule that accepts the traffic. -
05/03/2026 Keenetic RMM New Added a "Web apps" tab on the Client details page. To view the page, click on the Client name Added a system theme that adapts to the theme selected on the device Added colour indication for the button that opens the web interface in the context menu Added display of the “IPv6 in IPv4” interface Added a hint on the Site details page for the “SSL connection failure” error when the SSL certificate is invalid Fixed Fixed automatic addition of a new user to a team after joining via an invitation link and completing registration Fixed layout on the Dashboard page Fixed layout in the Add site and Import sites modal windows Updated the design of the Details tab on the Site details page Updated the design of the Settings page Fixed the display of a date selection interface on the Event Log page Fixed the appearance of redundant entries in the Event log when rebooting the extender or updating its OS
-
05/03/2026 Keenetic RMM Automatic OS update: configuration options for sites A new "Operations" tab is now available on the Site details page, where you can change the OS update channel and select the update schedule Added group operations for configuring automatic OS updates on the Sites page Added display of the "Update сhannel" and "Auto-update schedule" in the corresponding columns on the Sites page Please review the articles “Updating the OS on all Mesh Wi-Fi System nodes” and “KeeneticOS automatic updates” before getting started
-
05/03/2026 Keenetic RMM CLI tool: convenient site management Discover the simplicity of the CLI tool. Save, edit and apply commands on selected sites with the ability to create templates. Learn more & get started Leave feedback
-
Unfortunately, there is a bug in the Alpha 3, related to the firmware update process. I suggest that you use the recovery utility described here: https://support.keenetic.com/sprinter/kn-3710/en/21740.html#21740-keeneticos-recovery And then you should be able to update to Alpha 4, where this issue is fixed. The link above is for KN-3710, you can find the recovery utility relevant to your particular model, by entering it's name here: https://support.keenetic.com/ and then searching for "Restore".
-
The problem occurs periodically. Usually it either connects to all or none. I can provide you with service numbers, but there are a lot of routers, do I need to list them all? The problem usually occurs from a mobile phone on the road, from home, from the office at a certain time.