-
Posts
937 -
Joined
-
Last visited
-
Days Won
3
Content Type
Profiles
Forums
Gallery
Downloads
Blogs
Events
Posts posted by dexter
-
-
@Вежливый Снайпер, вам сюда
-
 1
1
-
-
А зачем это нужно в режиме ТД? Должно считаться на головном роутере, а не на ТД или тому подобному.
-
@Infy, после того как с консоли ещё раз указал draft все нормально обновилось. Глюк какой-то.
-
@Kiborg_Man, как победили?
-
Сегодня обновлял на новый драфт свои устройства. На ultra 1 через вэб морду была доступна 2.13.C.0.0-0.
Решил обновить через консоль, так она и обновилась до выше указанной прошивки.
Не знаю какая нужна инфа для отладки?
-
 1
1
-
-
U2, U1 и Extra 2 монитор трафика работает.
-
Вроде заработал. Только часть на аглицком осталась не переведенная.
-
@eralde, ошибки есть.
Failed to load resource: the server responded with a status of 401 (Unauthorized) login#goto=%2Fdashboard:1 This page includes a password or credit card input in a non-secure context. A warning has been added to the URL bar. For more information, see https://goo.gl/zmWq3m. 3auth:1 Failed to load resource: the server responded with a status of 401 (Unauthorized) 2vendor-9968608500.js:12 TypeError: Cannot read property 'hosts' of undefined at app-df5167aeb7.js:3 at app-df5167aeb7.js:3 at Array.forEach (<anonymous>) at app-df5167aeb7.js:3 at vendor-9968608500.js:12 at vendor-9968608500.js:12 at l.$eval (vendor-9968608500.js:12) at l.$digest (vendor-9968608500.js:12) at l.$apply (vendor-9968608500.js:12) at vendor-9968608500.js:12 (anonymous) @ vendor-9968608500.js:12
Может Вам VPN доступ дать?
Работаю в Opera 55.0.2994.61
В крайнем Хроме такая же фигня.
-
Выяснил, что ломает главную страницу.
interface GigabitEthernet0/Vlan101 rename Vlan101 description Vlan-101 mac address 58:8b:f3:66:88:11 security-level private ip address 192.168.101.254 255.255.255.0 ip dhcp client dns-routes ip dhcp client name-servers upИ после этого видим то, что в первом посте.
Делаем интерфейс "down" и все ОК. Если делаем "security-level protected" так же ломается главная страница. Не ломается она только при "security-level public".
Так, что про мусор в конфиге тут говорить не уместно. У меня роутер используется как роутер, а не как комбайн с трансмшен и подобными компонентами.
-
 2
2
-
 1
1
-
-
Вы меня сейчас до мотивируете до полного сброса, что бы я сам докопался, что ломает главную страницу. Благо погода говно и никуда идти не нужно.
-
Тем более.
-
А почему бы не полезть? Если оно до определенного момента работало, затем на всех 3х устройствах с далеко не стандартными конфигами приобрело такой вид. 2.13 сейчас в бете, но картина не меняется.
Лучше выловить такое поведение как можно ранее, чем это потом вылезет у кого-то в оф релизе.
Это тянется с версии 2.13.A.3.0-0:
https://forum.keenetic.net/topic/4929-ошибки-web/?do=findComment&comment=57935
p.s. там на 2.14 была проблема со страницей общих настроек в виде белого листа, откатывался на 2.13 через консоль.
-
 3
3
-
-
-
-
19 августа в 23:50 перестал работать IPIP туннель между U2(сервер) и U1(клиент).
В данный момент селф-тест могу снять только с U2, вечером смогу снять и с U1.
Ниже скрытым постом будут логи с кинетиков.
-
2 часа назад, KorDen сказал:
Ну очевидно же что опечатка, там otd на самом деле
interface Bridge0 iapp key test
Почему же?
interface WifiMaster0/AccessPoint0 rename AccessPointТут iapp отсутствует.
(config)> interface Bridge0 i inherit - add Ethernet interface to a Bridge (with inheritance) include - add Ethernet interface to a Bridge ip - configure IP parameters igmp - configure IGMP parameters ipsec - configure IPsec parameters (config)> interface Bridge0 iПро опечатку сам догадался, но разработчикам сообщить нужно.
-
Обидно. Тогда лучше полностью выпиливать функционал команд.
На Экстра 2 "iapp" есть, а "ft ods" отсутствует.
Нужен список моделей на которых работает.
-
Настраивая роуминг на данном роутере в консоле
(config)> interface AccessPoint ft ods Command::Base error[7405600]: no such command: ods. (config)> interface AccessPoint ft mdid - set FT MDID otd - enable Fast Transition Over-the-DS enable - enable Fast Transition (config)> interface AccessPoint ftи еще
(config)> interface Bridge0 iapp (config)> interface Bridge0 iapp test Command::Base error[7405600]: no such command: test. (config)> -
Подтверждаю.
-
7 часов назад, eralde сказал:
Ошибка, из-за которой интерфейс не работал в IE11 уже исправлена в A.3.0-4.
Проверьте, пожалуйста.
Работает.
-
 1
1
-
-
Хорошо, но с того момента не одного отвала не было.
-
Прикладываю лог файлом. Читать снизу. Началось все гораздо ранее.
И кусочек лога перед перезагрузкой по питанию.
Скрытый текст2018-07-30 08:18:25,"0","4","border.home","ndm:","","1"," kernel: mroute: pending queue full, dropping entries" 2018-07-30 08:18:11,"1","4","border.home","ndm:","","1"," Core::Watchdog: Event sender holds CORE (2) lock 7625 seconds acquired Jul 30 06:11:04." 2018-07-30 08:18:10,"1","4","border.home","ndm:","","1"," Core::Watchdog: Main holds CORE (2) lock 7680 seconds acquired Jul 30 06:10:08." 2018-07-30 08:18:10,"1","4","border.home","ndm:","","1"," Core::Watchdog: Timer holds CORE (2) lock 7736 seconds acquired Jul 30 06:09:12." 2018-07-30 08:18:09,"1","4","border.home","ndm:","","1"," Core::Watchdog: Statistics collector thread holds INTERFACE_PART (64) lock 7740 seconds acquired Jul 30 06:09:08." 2018-07-30 08:18:09,"1","4","border.home","ndm:","","1"," Core::Watchdog: Interface Bridge0 IPv4 neighbour explorer holds ARP_TABLE (108) lock 7740 seconds acquired Jul 30 06:09:09." 2018-07-30 08:17:31,"0","4","border.home","ndm:","","1"," kernel: mroute: pending queue full, dropping entries" 2018-07-30 08:17:11,"1","4","border.home","ndm:","","1"," Core::Watchdog: Event sender holds CORE (2) lock 7565 seconds acquired Jul 30 06:11:04." 2018-07-30 08:17:10,"1","4","border.home","ndm:","","1"," Core::Watchdog: Main holds CORE (2) lock 7620 seconds acquired Jul 30 06:10:08." 2018-07-30 08:17:10,"1","4","border.home","ndm:","","1"," Core::Watchdog: Timer holds CORE (2) lock 7676 seconds acquired Jul 30 06:09:12." 2018-07-30 08:17:09,"1","4","border.home","ndm:","","1"," Core::Watchdog: Statistics collector thread holds INTERFACE_PART (64) lock 7680 seconds acquired Jul 30 06:09:08." 2018-07-30 08:17:09,"1","4","border.home","ndm:","","1"," Core::Watchdog: Interface Bridge0 IPv4 neighbour explorer holds ARP_TABLE (108) lock 7680 seconds acquired Jul 30 06:09:09." 2018-07-30 08:17:08,"0","4","border.home","ndm:","","1"," kernel: " 2018-07-30 08:17:08,"0","4","border.home","ndm:","","1"," kernel: [<8001453c>] stack_done+0x20/0x44" 2018-07-30 08:17:08,"0","4","border.home","ndm:","","1"," kernel: [<800a3cf8>] sys_mmap_pgoff+0x8c/0x168" 2018-07-30 08:17:08,"0","4","border.home","ndm:","","1"," kernel: [<800a31cc>] mmap_region+0x1ec/0x748" 2018-07-30 08:17:08,"0","4","border.home","ndm:","","1"," kernel: [<800a237c>] do_munmap+0x240/0x3e0" 2018-07-30 08:17:08,"0","4","border.home","ndm:","","1"," kernel: [<800a14a0>] unmap_region+0xe4/0x12c" 2018-07-30 08:17:08,"0","4","border.home","ndm:","","1"," kernel: [<8009bb60>] free_pgtables+0x58/0x138" 2018-07-30 08:17:08,"0","4","border.home","ndm:","","1"," kernel: [<800a19cc>] unlink_file_vma+0x44/0x80" 2018-07-30 08:17:08,"0","4","border.home","ndm:","","1"," kernel: [<8014c328>] prio_tree_remove+0x94/0x138" 2018-07-30 08:17:08,"0","4","border.home","ndm:","","1"," kernel: [<8000b010>] ret_from_irq+0x0/0x4" 2018-07-30 08:17:08,"0","4","border.home","ndm:","","1"," kernel: [<8000cbe0>] do_IRQ+0x18/0x28" 2018-07-30 08:17:08,"0","4","border.home","ndm:","","1"," kernel: [<8007377c>] generic_handle_irq+0x3c/0x54" 2018-07-30 08:17:08,"0","4","border.home","ndm:","","1"," kernel: [<80077c70>] handle_percpu_irq+0x8c/0xbc" 2018-07-30 08:17:08,"0","4","border.home","ndm:","","1"," kernel: [<80074138>] handle_irq_event_percpu+0x70/0x1fc" 2018-07-30 08:17:08,"0","4","border.home","ndm:","","1"," kernel: [<80011970>] c0_compare_interrupt+0x74/0x88" 2018-07-30 08:17:08,"0","4","border.home","ndm:","","1"," kernel: [<8004cd70>] hrtimer_interrupt+0x188/0x4bc" 2018-07-30 08:17:08,"0","4","border.home","ndm:","","1"," kernel: [<8004c130>] __run_hrtimer.isra.5+0x68/0x138" 2018-07-30 08:17:08,"0","4","border.home","ndm:","","1"," kernel: [<8006792c>] tick_sched_timer+0x7c/0x338" 2018-07-30 08:17:08,"0","4","border.home","ndm:","","1"," kernel: [<80035c1c>] update_process_times+0x48/0x74" 2018-07-30 08:17:08,"0","4","border.home","ndm:","","1"," kernel: [<8007bc04>] rcu_check_callbacks+0x98/0x160" 2018-07-30 08:17:08,"0","4","border.home","ndm:","","1"," kernel: [<8007ac14>] __rcu_pending+0x1dc/0x540" 2018-07-30 08:17:08,"0","4","border.home","ndm:","","1"," kernel: [<802e5144>] dump_stack+0x8/0x34" 2018-07-30 08:17:08,"0","4","border.home","ndm:","","1"," kernel: Call Trace:" 2018-07-30 08:17:08,"0","4","border.home","ndm:","","1"," kernel: (t=3075347 jiffies)" 2018-07-30 08:17:08,"0","3","border.home","ndm:","","1"," kernel: INFO: Stall ended before state dump start" 2018-07-30 08:17:08,"0","3","border.home","ndm:","","1"," kernel: INFO: rcu_sched detected stalls on CPUs/tasks: { 2} (detected by 0, t=3075342 jiffies)" 2018-07-30 08:17:08,"0","3","border.home","ndm:","","1"," kernel: INFO: rcu_sched self-detected stall on CPU { 2} " 2018-07-30 08:16:24,"0","4","border.home","ndm:","","1"," kernel: mroute: pending queue full, dropping entries" 2018-07-30 08:16:11,"1","4","border.home","ndm:","","1"," Core::Watchdog: Event sender holds CORE (2) lock 7505 seconds acquired Jul 30 06:11:04." 2018-07-30 08:16:10,"1","4","border.home","ndm:","","1"," Core::Watchdog: Main holds CORE (2) lock 7560 seconds acquired Jul 30 06:10:08." 2018-07-30 08:16:10,"1","4","border.home","ndm:","","1"," Core::Watchdog: Timer holds CORE (2) lock 7616 seconds acquired Jul 30 06:09:12." 2018-07-30 08:16:09,"1","4","border.home","ndm:","","1"," Core::Watchdog: Statistics collector thread holds INTERFACE_PART (64) lock 7620 seconds acquired Jul 30 06:09:08." 2018-07-30 08:16:09,"1","4","border.home","ndm:","","1"," Core::Watchdog: Interface Bridge0 IPv4 neighbour explorer holds ARP_TABLE (108) lock 7620 seconds acquired Jul 30 06:09:09." 2018-07-30 08:15:31,"0","4","border.home","ndm:","","1"," kernel: mroute: pending queue full, dropping entries" 2018-07-30 08:15:11,"1","4","border.home","ndm:","","1"," Core::Watchdog: Event sender holds CORE (2) lock 7445 seconds acquired Jul 30 06:11:04." 2018-07-30 08:15:10,"1","4","border.home","ndm:","","1"," Core::Watchdog: Main holds CORE (2) lock 7500 seconds acquired Jul 30 06:10:08." 2018-07-30 08:15:10,"1","4","border.home","ndm:","","1"," Core::Watchdog: Timer holds CORE (2) lock 7556 seconds acquired Jul 30 06:09:12." 2018-07-30 08:15:09,"1","4","border.home","ndm:","","1"," Core::Watchdog: Statistics collector thread holds INTERFACE_PART (64) lock 7560 seconds acquired Jul 30 06:09:08." -
На первой ультра такого не замечал. Подключение у обоих IPoE.
to NDM team, если логи не полные или нужно больше подробностей, могу дать доступ к своему сислог серверу.
-
Есть оборудование вэб интерфейс которых работает только в IE за счет плагинов. Сам IE не использую.



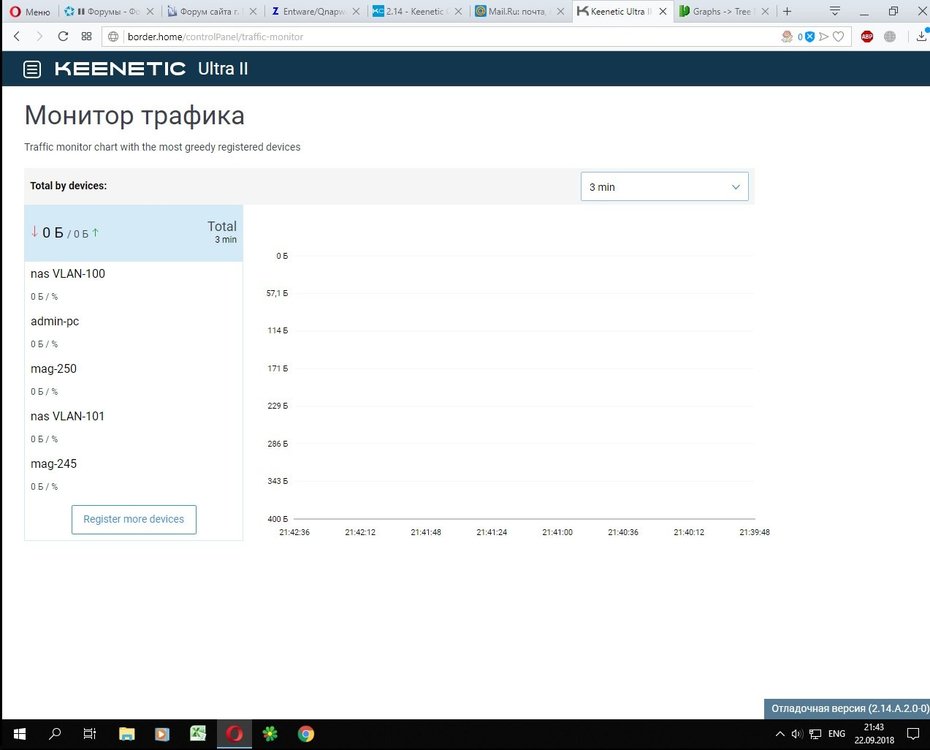
Упал IP-IP туннель между U2 и U1 на 2.14.A.2.0-1
in 2.14
Posted
Второй раз ловлю такое, что туннель перестает работать. При этом железки не ребутаются и на удаленный сислог сервер успевает попадать инфа от удаленной U1. U2 в данном решении является сервером.
Ниже прикладываю 2 селф-теста.
Отвалилось все в 12:50, восстановилось само в 16:25.
Оба Кинетика находятся в единой сети провайдера и имеют белые IP.