Leaderboard
Popular Content
Showing content with the highest reputation since 02/26/25 in all areas
-
@Pars @PriSonerS61 @ru.celebi @Ahmed Ensar, thank you for your help. The issue is confirmed, it will be fixed in one of the future versions.5 points
-
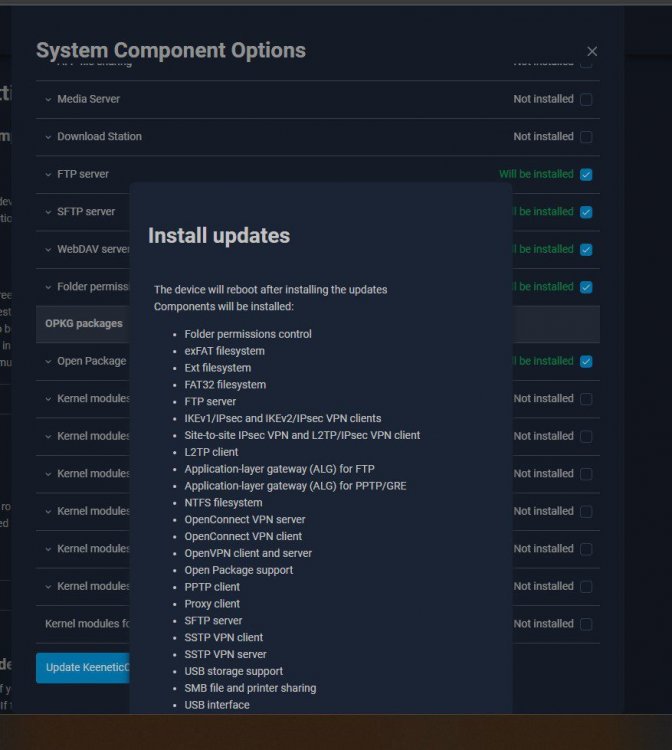
Release 4.3.0 (preview): Cifs: removed "CIFS" suffix from the mDNS name of the device [NDM-3648] IP: implemented deletion of routes by “route delete” command when importing from a bat-file (reported by @VVS) [NDM-3778] IPv6: implemented DNS server configuration for subnets [NDM-3702]: ipv6 subnet {name} dns-server ({address1} [address2] | disable) Web: fixed absence of buttons on the confirmation popup dialog in the Fail-safe mode (reported by @vk11) [NWI-4143] Web: fixed appearance of the "Read more" button in the list of knowledge base articles (reported by @VVS) [NWI-4137] Web: fixed Applications page loading error [NWI-4104] Web: fixed color of the separation line on the "Network Ports" tile [NWI-4145] Web: fixed excessive row height in the Client Lists table (reported by @AndreBA) [NWI-4133] Web: fixed issues caused by updating the style of control elements (reported by @dimon27254) [NWI-4140] Web: fixed issues in the mobile version of the Connection Policies page (reported by @dimon27254) [NWI-4114] Web: fixed line spacing in text annotations in the mobile version (reported by @dimon27254) [NWI-3872] Web: fixed saving of the main menu in a hidden state when closing and reopening the browser window (reported by @cheburashkaDDNS) [NWI-4120] Web: fixed selection of segments on the traffic monitor pie chart in the mobile version (reported by @dimon27254) [NWI-4079] Web: redesigned "My networks and Wi-Fi" tile on the dashboard [NWI-4071] Wi-Fi: fixed transfer of multicast and broadcast traffic when client isolation is enabled on mt7981-based devices [SYS-1329]5 points
-
Release 4.3.2 (preview): DNS: fixed behavior of an empty DNS profile [NDM-3843] IPoE: fixed IP address loss on the Home segment when setting port 1 as WAN on KN-3910 [NDM-3830] IPsec: fixed access to the bound network segment for L2TP/IPsec VPN clients [NDM-3715] OpenConnect: fixed compatibility with VPN Client Pro for Android (reported by @Mechanics) [NDM-3838] Opkg: fixed running single commands via "ndmc" (reported by @spatiumstas) [NDM-3837] USB: added support for Fibocom FM190W modem [NDM-3849] Web: fixed various bugs in the interface (reported by @spatiumstas, @dimon27254, @iggo) [NWI-4214]: NWI-4178, NWI-4013, NWI-4187, NWI-4194, NWI-4196, NWI-4197, NWI-4004 Wi-Fi: fixed wireless client disconnection by timeout on AX3000 access points [SYS-1337] ZeroTier: fixed identity.public validation for big-endian (mips) devices (reported by @gaaronk) [NDM-3821]4 points
-
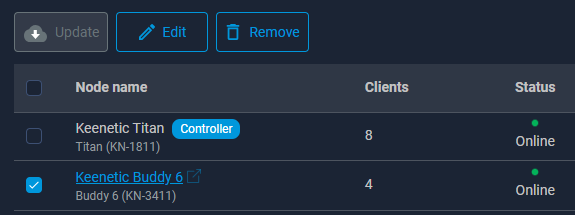
Please consider adding a "Reboot" button next to the existing Edit and Remove buttons in the mesh device management interface. Currently, restarting a mesh node requires logging into each device separately, which is inefficient and time-consuming. Suggested Placement: [Update] [Edit] [Remove] [Reboot] This addition would make it much easier to manage and restart mesh nodes directly from the controller interface.4 points
-
Release 4.3 Beta 2 (preview): DNS: implemented subdomain resolution in "object-group fqdn" (reported by @avn) [NDM-3726] HTTP: fixed Cookie handling and related "Core::Scgi::Tools: bad request: no session" error during authorization (reported by @snark) [NDM-3713] HTTP: fixed missing static DNS records when "ip http proxy dns-override" is enabled (reported by @Leshiyart) [NDM-3718] IPv6: fixed 6in4 tunnel performance when hardware packet engine is enabled [SYS-1271] OpenSSL: updated to 3.3.3 [SYS-1306] Proxy: fixed resetting of interface counters when it is shut down (reported by @keenet07) [NDM-3724] SFP: fixed KN-1012 compatibility with RTL9601D-based SFP modules [SYS-1313] Web: fixed redundant warning about unsaved changes during firmware upgrade (reported by @dimon27254) [NWI-3944] Web: fixed showing a scroll-bar when dragging objects in the connection priority list (reported by @dimon27254) [NWI-4044] Web: fixed showing an alert about unset password when it's already set (reported by @dimon27254) [NWI-4033] Web: fixed status showing not inserted SIM card on the dashboard (reported by @spatiumstas) [NWI-4016] Web: fixed tooltip readability in the Application Traffic Analyser table (reported by @dimon27254) [NWI-4020] Web: fixed unexpected second reboot after a system update (reported by @spatiumstas) [NWI-4047] Web: fixed Wi-Fi network shutdown despite canceling this action in a pop-up dialog box (reported by @dimon27254) [NWI-4010] Web: improved appearance of the side menu [NWI-3839] Web: locked the LTE signal metrics button when no connection is established (reported by @spatiumstas) [NWI-4015] Web: redesigned password input field with indication of password strength [NWI-4030]4 points
-
5.1 is an experimental branch, see also changelog 5.0. Supported models: Giga (KN-1010) Hero (KN-1011, KN-1012) Start/Starter (KN-1111, KN-1112, KN-1121) Air/Explorer (KN-1613, KN-1621) Extra/Carrier (KN-1711, KN-1713, KN-1714, KN-1721) Ultra/Titan (KN-1810, KN-1811, KN-1812) Viva/Skipper (KN-1910, KN-1912, KN-1913) Omni DSL (KN-2011, KN-2012) Extra DSL/Carrier DSL/Skipper/Speedster DSL (KN-2111, KN-2112, KN-2113) Runner 4G (KN-2210, KN-2211, KN-2212, KN-2213) Hero 4G (KN-2310, KN-2311) Hopper 4G+ (KN-2312) Hero DSL (KN-2410) Peak DSL (KN-2510) Giant (KN-2610) Peak (KN-2710) Orbiter Pro (KN-2810) Skipper 4G (KN-2910) Speedster 4G (KN-2911) Speedster (KN-3010, KN-3012, KN-3013) Buddy 4 (KN-3210, KN-3211) Buddy 5 (KN-3310, KN-3311) Buddy 5S (KN-3410) Buddy 6 (KN-3411) Voyager Pro (KN-3510) Hopper DSL (KN-3610, KN-3611) Sprinter (KN-3710, KN-3711) Sprinter SE (KN-3712) Hopper (KN-3810, KN-3811) Hopper SE (KN-3812) Challenger (KN-3910) Challenger SE (KN-3911) Racer (KN-4010) Buddy 6 SE (KN-4410) Explorer 4G (KN-4910) Orbiter 6 (KAP-630)3 points
-
Release 5.0.5 (preview): IP: fixed flushing cached sessions when restarting Wireguard connection included in a routing policy [NDM-4225] KeenDNS: fixed direct domain name resolution via IPv6 [NDM-4136] UPnP: fixed compatibility with Synology NAS (reported by @Gull_88) [NDM-4247] UsbQmi: added support for Sierra EM9293 modem (reported by @Marvin) [NDM-4235] Web: fixed "Сaptive portal profiles not received" error [NWI-4611] Web: fixed displaying an empty dialog when file uploading is cancelled (reported by @spatiumstas) [NWI-4607]3 points
-
Release 5.0.4 (preview → stable): CIFS: fixed compatibility with MacOS TimeMachine [NDM-4112] gnutls: updated to 3.8.11 [NDM-4205]: CVE-2025-32988 CVE-2025-32989 CVE-2025-32990 CVE-2025-6395 CVE-2025-9820 HTTP: fixed loss of access to Web UI due to network discovery timeouts [NDM-4223] IP: fixed adding of static routes after the default route [NDM-4209] NTCE: optimized memory consumption [NDM-4219] SSDP: fixed system crash during network discovery [NDM-4224] Web: added Name sorting to DNS-Based Routing [NWI-4595] Web: fixed configuration saving without VLAN ID (reported by @Mikhail_YAR) [NWI-4578]3 points
-
The controller update channel is not propagated to the extender devices, this is the expected behavior.3 points
-
Release 5.0.3 (preview): DNS: fixed FQDN-based routing when DNS is running over TCP (reported by @qmxocynjca) [NDM-4201] DNS: optimized performance of FQDN routing list updates [NDM-4197] MWS: fixed wireless 2.4 GHz backhaul on MT7603 and MT7628-based devices [SYS-1513] udpxy: fixed crash when running on a Bridge public interface [NDM-4200] Web: fixed hiding the Mobile menu when USB modem support is not installed (reported by @qmxocynjca) [NWI-4518] ZeroTier: fixed system restart loop when fail-safe mode is enabled [NDM-4187]3 points
-
Release 5.0 Beta 2 (preview): CIFS: fixed excessive restarts when running a Wireguard server (reported by @dimon27254) [NDM-4059] DNS: fixed a busy loop when processing malformed responses (reported by @vitalik6243) [NDM-4034] DNS: fixed the operation of exclusive routes (reported by @keenet07) [NDM-4046] IPv6: fixed access to services running on interfaces with “private” security level (reported by @KirillR) [NDM-4061] OpenConnect: enabled support for Basic authentication [NDM-4037]: interface {name} openconnect allow-basic-auth SFP: fixed hardware reset of embedded switch on KN-1012 when using an external xPON SFP module [SYS-1455] Web: added IPv6 settings to Segments [NWI-4373] Web: allowed USSD requests starting with # [NWI-4401] Web: fixed display of segment access points after deletion (reported by @Sh1kuren) [NWI-4407] Web: fixed DNS profile editing when the "dns-filter" component is not installed (reported by @dimon27254) [NWI-4396] Web: fixed interface display when editing DNS-based routes (reported by @ftn453) [NWI-4405] Web: fixed KeenDNS configuration (reported by @ftn453) [NWI-4427] Web: fixed printing of Wi-Fi information with a custom logo (reported by @dimon27254) [NWI-4387] Web: fixed sorting of tables by ports and profiles (reported by @Серов Николай) [NWI-4386] Web: fixed static routing configuration issues (reported by @Denis P) [NWI-4428] Web: fixed validation of iperf3 parameters (reported by @dimon27254) [NWI-4402] Web: implemented the new Internet card on the dashboard [NWI-4377] Web: improved the naming of WireGuard configuration files (reported by @dimon27254) [NWI-4424] Wi-Fi: fixed blocking of legacy b/g clients when n/ax compatibility mode is configured [SYS-1446] Wireguard: fixed display of remote peers' IP addresses and ports (reported by @Denis P) [NDM-4064]3 points
-
Release 5.0 Beta 1 (preview): Ethernet: fixed bogus half-duplex link status for 2.5 Gbps [SYS-1438] IPsec: fixed "identity-local" reset during reconfiguration [NDM-4036] MWS: implemented the use of an Extender's built-in 4G modem as a WAN connection [NDM-4027] USB: fixed "invalid argument" error when polling SMART on SATA drives [NDM-4026] VRRP: imlpemented support for VRRP version 2 and 3; can be installed as a separate component [SYS-1443]: interface {name} vrrp group {group} ip {ip} — set virtual IP address for the group. interface {name} vrrp group {group} priority {priority} — set priority (integer in the range 0 to 255), the device with the numerically highest priority becomes the master in the group. interface {name} vrrp group {group} advertise {advertise} — set advertisement interval in seconds (integer in the range 1 to 255, the default is 1) interface {name} vrrp version {version} — set protocol version, supported values: default — use version 2 for IPv4 and version 3 for IPv6. v2 — strict compliance to VRRP version 2: zero VIPs are not allowed; IPv6 addresses not allowed; state MASTER can be configured if and only if priority is 255. v3 — compliance to VRRP version 3 for both IPv4 and IPv6. v3-compat — VRRP version 3 compatible with some manufacturers (e.g. Cisco and Juniper) who interpret RFC5798 5.2.8 as applying only to IPv6, since the pseudo-header in RFC2460 is specified only for IPv6, although most open source implementations include the pseudo-header for IPv4. This option enables the IPv4 pseudo-header, but excludes it from the checksum calculation for IPv4. show interface {name} vrrp — show VRRP status. Web: added IPv6 support on the Port Forwarding page [NWI-4213] Web: fixed issues with the WireGuard server configuration (reported by @dimon27254) [NWI-4372] Web: fixed issues with tooltips on the Wi-Fi system page (reported by @dimon27254) [NWI-4379] Web: fixed timestamp of the last WireGuard handshake (reported by @dimon27254) [NWI-4384]3 points
-
Release 5.0 Alpha 7: SNMP: added wireless broadband connection metrics [NDM-3934]: RSSI OID: .1.3.6.1.4.1.9.9.661.1.3.4.1.1.1.7006 RSRP OID: .1.3.6.1.4.1.9.9.817.1.1.1.1.1.1.7006 RSRQ OID: .1.3.6.1.4.1.9.9.817.1.1.1.1.1.2.7006 SNR OID: .1.3.6.1.4.1.9.9.817.1.1.1.1.1.3.7006 USB: implemented support for Signalinks M806B D525C modems [NDM-3933] Web: added cable testing display on Diagnostics page (reported by @dimon27254) [NWI-4029] Web: changed auto-update status on Extender (reported by @iggo) [NWI-4205] Web: fixed translation issues (reported by @dimon27254) [NWI-4281]3 points
-
Release 5.0 Alpha 6: DynDNS: fixed "IPv6 update disabled" issue while IPv6 address is present (reported by @ru.celebi) [NDM-3927] HTTP: fixed "ban remote host 127.0.0.1" error when using the mobile application [NDM-3926] IPsec: fixed binding IKEv2 policy to a home network segment (reported by @Denis P) [NDM-3925] IPsec: fixed rekey issue when initiating IKEv2 connection [NDM-3922] Web: fixed tooltip display on the Wi-Fi monitor tile (reported by @dimon27254) [NWI-4298] Web: improved function blocking during fail-safe operation [NWI-4252] Wireguard: fixed "system failed [0xcffd009e]" error when loading settings with rearranged [Peer] and [Interface] blocks (reported by @Sergeykk) [NDM-3930]3 points
-
Release 5.0 Alpha 5: IP: implemented removal of multiple routes; "no" destination arguments made optional [NDM-3911]: no ip route [{network} {mask} | {host} | default] [{gateway} | {interface}] [metric] no ip policy route [{network} {mask} | {host}] [{interface} | {gateway}] [metric] no ipv6 route [{prefix} | default] ({interface} [{gateway}] | {gateway}) IPv4: fixed "out of memory" error when creating an IP policy (reported by @Ponywka) [NDM-3907] Kernel: removed excessive debug messages from ntc [SYS-1384] mDNS: enabled announcement of the Web interface (HTTP) service in the local network [NDM-3919] OpenConnect: added nc (Juniper) protocol [NDM-3908]: interface {name} openconnect protocol (anyconnect | fortinet | nc) OpenConnect: fixed usage of authgroup with anyconnect protocol [NDM-3918] USB: fixed LTE modem's "terminal options verification failed" error (reported by @k19olegh68) [NDM-3905] Web: added a new Automatic theme that follows system preferences (requested by @dimon27254) [NWI-4242] Web: enabled usage of VLAN 0 for Wired connections [NWI-4315] Web: fixed appearance of table row borders (reported by @dimon27254) [NWI-4299] Web: fixed closing of the registration pop-up for unregistered hosts (reported by @spatiumstas) [NWI-4244] Web: fixed table scrolling on the Application Traffic Analyser page (reported by @dimon27254) [NWI-4283] Web: fixed table display in the Transition Log (reported by @dimon27254) [NWI-4284] Wi-Fi: fixed MAC address change for WifiStation interfaces (reported by @project_fcc) [NDM-3906] Wireguard: implemented obfuscation key for peers (requested by @Oleg Nekrylov) [NDM-3917]: interface {name} wireguard peer obfs-key {obfs-key} ZeroTier: removed repetitive "install accepted route" messages [NDM-3903]3 points
-
Release 4.3.4 (preview): IPv4: fixed "out of memory" error when creating an IP policy (reported by @Ponywka) [NDM-3907] IPv6: fixed inbound connections to SSH server (reported by @ru.celebi) [NDM-3891] IPv6: fixed inbound connections to VPN servers [NDM-3886] Kernel: removed excessive debug messages from ntc [SYS-1384] Web: added VLAN 802.1p settings to Ethernet Cable Connections (reported by @czerniewski) [NWI-3726] Web: fixed appearance of table row borders (reported by @AndreBA, @dimon27254) [NWI-4250, NWI-4299] Web: fixed color notations on the Traffic Monitor page (reported by @keenet07) [NWI-4243] Web: fixed device name display in WebCLI (reported by @qmxocynjca) [NWI-4240] Web: fixed minor issues with Mesh Wi-Fi system tile (reported by @dimon27254) [NWI-4275] Web: fixed saving of G.INP settings for ADSL [NWI-4270] Web: fixed saving of "TCP/UDP (all ports) and ICMP" forwarding rules [NWI-4253] Web: removed Users configuration description from "IKEv2/IPsec VPN server" page (reported by @project_fcc) [NWI-4245] Wi-Fi: fixed WPS when WPA2-Enterprise is enabled [SYS-1361] Wireguard: fixed AllowIPs validator to allow overlapping networks with a warning message (reported by @Александр Гольдварг) [NDM-3888] ZeroTier: removed repetitive "install accepted route" messages [NDM-3903]3 points
-
Release 5.0 Alpha 1: CWMP: implemented basic support of the TR-098 data model, transactions and STUN; feature is available on request, contact technical support for details [NDM-3870] Ethernet: fixed halting of packet transmission at 1 Gbps link on a 2.5 Gbps port [SYS-1354] IPv4: increased the object groups limit to 128 [NDM-3862] IPv6: implemented commands for static address and port translation rules [NDM-3819]: ipv6 static [protocol] ({interface} {mac} | {mac}) [{port} [through {end-port}] ] ipv6 static rule {index} (disable | schedule {schedule}) LTE: fixed USB device restart when ping-check is enabled [NDM-3848] Opkg: enabled auto-mounting of the /lib/system-modules directory (reported by @Kvark) [NDM-3693] Opkg: implemented OpkgTun and OpkgTap interfaces (reported by @avn) [NDM-3846] QMI: implemented the capability to include UsbQmi interfaces in bridge [NDM-3707] TSMB: removed obsolete "cifs master" command [NDM-3827] Web: implemented ZeroTier support in "Other connections" [NDM-4164] Wireguard: fixed AllowIPs validator to not allow overlapping networks [NDM-3868]3 points
-
Release 4.3 Beta 3 (preview): DNS: fixed "duplicate key: group" error when using FQDN object groups (reported by @dimon27254) [NDM-3755] HTTP: implemented blacklisting of remote hosts sending invalid POST requests [NDM-3716] NTCE: fixed "detected 5 attributes, only 4 supported" error (reported by @Strider78) [NDM-3756] OpenConnect: fixed User-Agent header when using "anyconnect" protocol [NDM-3733] SSTP: fixed access to SSTP VPN server when "ip http security-level private" is set [NDM-3747] USB: added support for Telit FN990 modem [NDM-3743] VPN: fixed WireGuard and OpenVPN port collision when creating tunnels [NDM-3732] Web: changed view of Connection Policies on mobile screens (reported by @dimon27254) [NWI-4049] Web: fixed display of SFP/Ethernet combo port connection mode (reported by @Gim12) [NWI-3319] Web: fixed opening Mesh Wi-Fi System page after a new Extender is acquired (reported by @KYTECHNGAMING) [NDM-3757] Web: fixed the inability to turn on the Ethernet port after it has been turned off [NWI-4066] Web: fixed unwanted reset of PPPoE authentication settings when selecting "Automatic (DHCP)" option (reported by @Leshiyart) [NWI-4065] Web: increased the number of visible options in drop-down lists (reported by @spatiumstas) [NWI-3756] Wi-Fi: fixed connection instability for some wireless client devices when "target-waketime" setting is enabled [SYS-1266] Wireguard: fixed losing "asc" settings after reconfiguration (reported by @FLK) [SYS-1320]3 points
-
5.0 is a stable branch, see also changelog 4.3. Supported models: Giga (KN-1010) Hero (KN-1011, KN-1012) Start/Starter (KN-1111, KN-1112, KN-1121) Air/Explorer (KN-1613, KN-1621) Extra/Carrier (KN-1711, KN-1713, KN-1714, KN-1721) Ultra/Titan (KN-1810, KN-1811, KN-1812) Viva/Skipper (KN-1910, KN-1912, KN-1913) Omni DSL (KN-2011, KN-2012) Extra DSL/Carrier DSL/Skipper/Speedster DSL (KN-2111, KN-2112, KN-2113) Runner 4G (KN-2210, KN-2211, KN-2212, KN-2213) Hero 4G (KN-2310, KN-2311) Hopper 4G+ (KN-2312) Hero DSL (KN-2410) Peak DSL (KN-2510) Giant (KN-2610) Peak (KN-2710) Orbiter Pro (KN-2810) Skipper 4G (KN-2910) Speedster 4G (KN-2911) Speedster (KN-3010, KN-3012, KN-3013) Buddy 4 (KN-3210, KN-3211) Buddy 5 (KN-3310, KN-3311) Buddy 5S (KN-3410) Buddy 6 (KN-3411) Voyager Pro (KN-3510) Hopper DSL (KN-3610, KN-3611) Sprinter (KN-3710, KN-3711) Sprinter SE (KN-3712) Hopper (KN-3810, KN-3811) Hopper SE (KN-3812) Challenger (KN-3910) Challenger SE (KN-3911) Racer (KN-4010) Hero 5G (KN-4110) Buddy 6 SE (KN-4410) Explorer 4G (KN-4910) Orbiter 6 (KAP-630)2 points
-
I'm trying to connect KN-1111 as Extender to my KN-3811 using Wi-Fi System. KN-1111 shown in "Extenders available for adding to the Wi-Fi System" but on "Acquire" nothing happens. Error from KN-3811 system log Mws::Controller::Manager: the controller DPN document is not accepted. I've tried to reset both devices, tried different os versions, reinstalled wifi system component, tried both ethernet and wps connection methods. No success.2 points
-
Release 5.0 Beta 3 (preview): CIFS: fixed copying files using named streams (reported by @dimon27254) [SYS-1450] DNS: added support for IP subnets in "object-group fqdn include" [NDM-4078] DNS: fixed forwarding of servfail.invalid requests to external servers [NDM-4069] DNS: fixed overload of "Dns::Route::ResolveQueue" [NDM-4086] DNS: reduced the resolving intensity of unused “object-group fqdn” names (reported by @dimon27254) [NDM-4082] IPsec: fixed transition of L2TP traffic when L2TP/IPsec server is running [NDM-4068] IPv4: fixed disabling of individual static routes (reported by @dimon27254) [NDM-4076] IPv6: enabled external access to backup WAN interfaces (reported by @qmxocynjca) [NDM-4067] VPN: implemented DNS server overriding for clients of built-in VPN servers [NDM-4032]: crypto map virtual-ip dns-servers {dns1} [dns2] crypto map l2tp-server dns-servers {dns1} [dns2] sstp-server dns-servers {dns1} [dns2] vpn-server dns-servers {dns1} [dns2] oc-server dns-servers {dns1} [dns2] Web: fixed blocking of Wi-Fi toggles in MWS extenders (reported by @dimon27254) [NWI-4450] Web: fixed display of application blocking status (reported by @FLK) [NDM-4051] Web: fixed display of drop-down lists on mobile screens (reported by @dimon27254) [NWI-4448] Web: fixed display of TunnelSixInFour interfaces when editing static rules (reported by @Denis P) [NWI-4456] Web: fixed display of WireGuard server statistics (reported by @Denis P) [NWI-4425] Web: fixed help sign jumping on mobile screens (reported by @dimon27254) [NWI-4447] Wi-Fi: fixed potential system crash when using OWE authentication [SYS-1461]2 points
-
Release 5.0 Beta 0: DNS: added support for subnets in "object-group fqdn exclude" (reported by @Denis P) [NDM-4013] Kernel: fixed security issues: CVE-2024-36971 [SYS-1436] CVE-2024-41012 [SYS-1430] CVE-2024-50302 [SYS-1431] SSH: fixed public access via IPv6 [NDM-4010] Web: added DNS-based routes feature to the Static routes page [NWI-4186] Web: added iperf3 tool to the Diagnostics page [NWI-4371] Web: redesigned DNS Configuration page for the mobile screens (reported by @dimon27254) [NWI-4375] Web: restored the lte-firmware file in the list of system files [NWI-4367]2 points
-
Release 5.0 Alpha 13: Core: added date and time to downloaded firmware and startup-config filenames (reported by @ftn453) [NDM-3999] DNS: added support for domain names in "object-group fqdn exclude" (reported by @keshun) [NDM-4001] DNS: fixed "ResolveQueue: system failed [0xcffd0046]" error (reported by @Denis P) [NDM-4002] Web: added Average speed information to the Traffic Monitor (reported by @enterfaza) [NWI-4212] Web: fixed DoH server validation (reported by @YevhenK) [NWI-4350] Web: fixed SFP port name saving [NWI-4360]2 points
-
Hello, I thought of a feature for experienced users. It is a process I often use in SFP GPON modules. It can be seen in Openwrt or Linux-based operating systems. I would like to see the ability to manually change partitions in KeeneticOS as well. One partition could hold the stable version, while the other partition could hold the developer version of KeeneticOS. Similarly, when updating from the developer version to the stable version during an update, the update should be written to the other partition. Instead of writing the new version to the other partition and performing the version update procedure each time, it would be a good idea to change the partition using a command line or a button in the interface. Example application: nv getenv sw_commit If sw_commit returns 0 sw_commit=0 nv setenv sw_commit 1 nv setenv sw_active 1 reboot - nv getenv sw_commit If sw_commit returns 1 sw_commit=1 nv setenv sw_commit 0 nv setenv sw_active 0 reboot If you want to manage this, you can also set up one partition to always have the stable version and the other partition to always have the developer version. Just switch to the other partition first when you want to update a specific software.2 points
-
Release 5.0 Alpha 12: CdcEthernet: added support for SMD12 SMW12 modems [NDM-2979] HTTP: implemented Origin header enforcement for proxies [NDM-3988]: ip http proxy {name} force-origin {force-origin} MWS: fixed regression after implementing user tag “manager” (reported by @dimon27254) [NDM-3981] USB: added support for Fibocom FM101-GL modem [NDM-3970] USB: added support for Olax F90 modem [NDM-3983] Web: fixed End User License Agreement line spacing (reported by @dimon27254) [NWI-4344]2 points
-
Having an RTMP server would be very useful. Could you please consider this? Keenetic becomes indispensable for live broadcasts. Matter support would be great, and for example, by connecting a Sonoff USB module to the Keenetic, you could manage all ZigBee, Wi-Fi, and Matter-enabled devices through the Keenetic.2 points
-
2 points
-
Release 5.0 Alpha 11: Core: implemented user tag "manager" for limited administration rights [NDM-3945] HTTP: fixed display of custom logo in the "Information for the Wi-Fi network" pop-up (reported by @dimon27254) [NDM-3969] Iperf: fixed configuration issues (reported by @ru.celebi, @vasek00) [NDM-3972] IPv6: implemented UPnP IGDv2 PCP protocol [NDM-3859] Web: added data transfer statistics to the IPsec table (reported by @sersh) [NWI-4318] Web: added "Application filtering" tab to the "Internet safety" settings [NWI-4232] Web: added Network access setting for IKEv1 and IKEv2 VPN servers [NWI-4328] Web: adjusted the WireGuard table look (reported by @FLK) [NWI-4337] Web: implemented WireGuard VPN server configuration in Applications [NWI-4206] Web: fixed IPv6 prefix validator in WireGuard (reported by @spatiumstas) [NWI-4355] Web: fixed issues when editing users and passwords (reported by @dimon27254) [NWI-4131] Web: fixed the behaviour of drop-down lists when clicked (reported by @dimon27254) [NWI-4365] Web: reduced the toggle response time on the Segments page (reported by @dimon27254) [NWI-4363]2 points
-
Release 5.0 Alpha 10: Core: implemented "Dummy" network interface [NDM-3958] DNS: fixed bugs in the operation of FQDN-based routing rules (reported by @dimon27254) [NDM-3956] DynDNS: implemented "dynu" service type (reported by @ru.celebi) [NDM-3959] Mobile: renamed "acq", "apn", and "wwan-force-connected" configuration commands [NDM-3950]: interface {name} usb acq → interface {name} mobile acq interface {name} usb apn → interface {name} mobile apn interface {name} usb wwan-force-connected → interface {name} mobile force-connected OpenConnect: fixed "system failed [0xcffd0085]" error by supporting IPv6 DNS (reported by @arsik) [NDM-3962] Opkg: implemented support for authentication credentials in "opkg disk" URL (reported by @dimon27254) [NDM-3960] Tools: added "reverse" and "streams" arguments to iperf3 [NDM-3963]: tools iperf3 {host} [ipv4 | ipv6] [tcp | udp] [reverse] [port {port}] [bitrate {bitrate}] [streams {streams}] [time {time} | bytes {bytes}] [source-interface {source-interface}] Tools: implemented "iperf3" service [NDM-3786]: iperf3 interface {interface} — bind to a specific interface (default: bind to all interfaces according to the security level) iperf3 port {port} — set port (default: 5201) iperf3 security-level (public | protected | private) — set security level (default: private) service iperf3 — run the service2 points
-
Release 5.0 Alpha 9: DNS: fixed priority of user-defined static records over dynamic ones [NDM-3947] DNS: implemented FQDN object-group based routing [NDM-3946]: dns-proxy route object-group {group} [{interface} | {gateway} [interface]] [auto] [reject] DynDNS: fixed simultaneous registration of IPv4 and IPv6 addresses (reported by @ru.celebi) [NDM-3952] IPsec: fixed transmission of Virtual-IP DHCP routes to VPN clients (reported by @lexm434) [NDM-3954] IPv6: fixed MAP-T bypass of UDP packets with zero checksum [SYS-1404] Syslog: fixed saving of "no system log reduction" to the running-config [NDM-3953] VPN: fixed OpenConnect, Proxy, ZeroTier client reconfiguration (reported by @qmxocynjca) [NDM-3951] Web: fixed display of the clients tooltip in the Wi-Fi system nodes table (reported by @zevs) [NWI-4323] Web: fixed saving of changed TTL value [NWI-4322] Web: fixed the display of the drop-down list on the Internet Safety page (reported by @kroleg) [NWI-4306] Web: hidden Home segment delete button (reported by @dimon27254) [NWI-4340] Web: speed up loading when no replies are received from webhelp (reported by @dimon27254) [NWI-4326] Wireguard: enabled peer "keepalive" interval set to 15 by default (reported by @FLK) [NDM-3948]2 points
-
Release 5.0 Alpha 8: IPv6: removed the "ip6" component; IPv6 functionality is merged with the base system [NDM-3935] Mobile: added eSIM local profile management support for UsbLte, UsbQmi interfaces [NDM-3850]: show interface {name} esim status — get eSIM status (incl. EID) interface {name} esim profile download {qrcode} — download eSIM profiles interface {name} esim profile list — list eSIM profiles interface {name} esim profile activate {iccid} — activate eSIM profile interface {name} esim profile deactivate {iccid} — deactivate eSIM profile interface {name} esim profile delete {iccid} — delete eSIM profile interface {name} esim profile rename {iccid} {newname} — rename eSIM profile Proxy: fixed "socks5 client read auth" error [NDM-3942] Tools: implemented "tools iperf3" command; must be installed as a separate component [NDM-3785]: tools iperf3 {host} [ipv4 | ipv6] [tcp | udp] [port {port}] [bitrate {bitrate}] [time {time} | bytes {bytes}] [source-interface {source-interface}] Web: added interface selection when downloading routes (requested by @vincome) [NWI-4288] Wireguard: fixed various configuration import issues [NDM-3943]2 points
-
Release 5.0 Alpha 4: Dns: fixed forwarding of negative responses to local clients at 127.0.0.1 (reported by @dchusovitin) [SYS-1382] Web: fixed appearance of table row borders (reported by @AndreBA) [NWI-4250] Web: fixed behavior of the menu items in expanded view (reported by @dimon27254) [NWI-4198] Web: fixed device name display in WebCLI (reported by @qmxocynjca) [NWI-4240] Web: fixed minor issues with Mesh Wi-Fi system tile (reported by @dimon27254) [NWI-4275] Web: fixed saving of "TCP/UDP (all ports) and ICMP" forwarding rules [NWI-4253]2 points
-
Release 5.0 Alpha 3: IPv4: implemented support for comments when importing/exporting routes (reported by @SergiusWA) [NDM-3889] IPv6: fixed inbound connections to SSH server (reported by @ru.celebi) [NDM-3891] IPv6: fixed inbound connections to VPN servers [NDM-3886] Web: added VLAN 802.1p settings to Ethernet Cable Connections (reported by @czerniewski) [NWI-3726] Web: fixed color notations on the Traffic Monitor page (reported by @keenet07) [NWI-4243] Web: removed Users configuration description from "IKEv2/IPsec VPN server" page (reported by @project_fcc) [NWI-4245] Wireguard: fixed AllowIPs validator to allow overlapping networks with a warning message (reported by @Александр Гольдварг) [NDM-3888] Wireguard: fixed WGOBFS netfilter chains (reported by @Denis P) [NDM-3890]2 points
-
Release 5.0 Alpha 2: IPsec: fixed an issue with IKEv1 and IPsec Site-to-Site server running simultaneously [NDM-3878] IPsec: fixed segmentation fault for VirtualIPServerIKE2 [NDM-3880] IPsec: fixed traffic accounting for IKEv2 server [NDM-3876] IPsec: implemented usage of IKEv2 server certificate defined by "crypto ipsec profile VirtualIPServerIKE2 identity-local fqdn" (requested by @Denis P) [NDM-3884] Proxy: removed "Proxy0: 0x7f9ba28be0 socks5 client res.rep” debug messages from the system log [NDM-3875] Web: fixed saving of G.INP settings for ADSL [NWI-4270] Wi-Fi: fixed WPS when WPA2-Enterprise is enabled [SYS-1361] Wireguard: implemented DD-WRT compatible obfuscation key (requested by @Oleg Nekrylov) [NDM-3883]: interface {name} wireguard obfs-key {obfs-key}2 points
-
Once upon a time ago reboot button is requested 😁2 points
-
Now, both on the http://192.168.1.1/wifi-monitor/utilization tab and on the widget, you can alternately view the load of the selected channel, i.e. choosing either 2.4 GHz or 5 GHz. I would like to be able to view both ranges simultaneously, both on the widget and on the tab!!!2 points
-
Release 4.3.1 (preview): DynDNS: fixed saving of 'dyndns nobind' setting [NDM-3816] HTTP: fixed redundant disclosure device information [NDM-3783]: CVE-2024-4021 CVE-2024-4022 IP: fixed applying static routes in multiple IP policies [NDM-3814] IP: fixed assignment of "conform" policy after automatic client registration [NDM-3810] IPsec: fixed wrong "crypto map" use in L2TP/IPSec server settings [NDM-3811] OpenConnect: added random padding to packets to improve connection resistance (reported by @dimon27254) [NDM-3791] OpenConnect: fixed access to the VPN server's attached network [NDM-3820] TSMB: enabled support for extended attributes (reported by @dimon27254) [NDM-3645] VPN: added 'session-logout' command to terminate VPN sessions (reported by @CBLoner) [NDM-3788]: crypto map l2tp-server session-logout {session} crypto map virtual-ip session-logout {session} sstp-server session-logout {session} vpn-server session-logout {session} oc-server session-logout {session} Web: added "https://" to OpenConnect VPN server URI when camouflage is enabled [NWI-4146] Web: added alphabetical sorting to Policy Bindings [NWI-4092] Web: fixed various bugs and layout issues on different screen sizes (reported by @dimon27254, @spatiumstas, @enterfaza, @FLK, @mrGhotius) [NWI-4191]: NWI-4168, NWI-4161, NWI-3901, NWI-4108, NWI-3922, NWI-4083, NWI-4085, NWI-4122, NWI-4125, NWI-4136, NWI-4134, NWI-4135, NWI-4139, NWI-4141, NWI-4130, NWI-4169, NWI-4080, NWI-4160, NWI-4151 Web: implemented display of users in file ACLs for which the system has no accounts configured [NWI-3951]2 points
-
Hello, @alasedo. The data that our devices collect is listed here: https://keenetic.com/en/legal#dpn. Even if you have disabled the cloud features and service to communicate with the mobile app, there is still data transmission for the Authenticity Status Verification and the Internet Checker feature as outlined in the document. You can disable the Internet Checker, by executing the following commands: no service internet-checker system configuration save However, it is not possible to disable data transmission that is used for the authenticity verification purposes.2 points
-
There is a problem with the grid layout in Edge, but everything looks normal in Firefox.2 points
-
Release 4.3 Beta 4 (preview): IGMP: fixed multicast forwarding to IPTV ports [NDM-3767] IPsec: fixed adding route to client network on L2TP/IPsec server [NDM-3758] NTCE: fixed "system failed [0xcffd00bd]" error when saving filtering profiles (reported by @dimon27254) [NDM-3770] Web: fixed mandatory password input when creating a user for OPKG and applications (reported by @spatiumstas) [NWI-3700] Web: fixed tooltip behaviour on Mesh Wi-Fi system card [NWI-4062] Wi-Fi: fixed configuration of channel width [NDM-3764] Wi-Fi: fixed connection issues with Intel AC9260/9560 adapters in WPA3 PSK mode [SYS-1325]2 points
-
2 points
-
Hello, Enrico! Yes, it is possible to send and list received SMS via the REST API. The easiest way to do it is to see how the web interface interacts with the router. I wrote an extended explanation for USSD requests here: Commands for reading/sending SMS are quite similar (sms {interface} list, sms {interface} send, sms {interface} delete, sms {inteface} read). A simple example: A few extra notes: - you need to be authorized on the Keenetic to send the requests; the auth process is described here (in Russian): https://forum.keenetic.ru/topic/5461-не-работает-digest-авторизация-для-rci/#findComment-62946 preserve session cookies while sending follow-up GET requests - don't forget to set the Content-Type HTTP header for your requests (Content-Type: application/json)2 points
-
2 points
-
The main idea is to add the ability to reject connections based on MAC address patterns (masks) in cases where white/blacklists are not flexible enough for configuration.2 points
-
So the real feature request sounds as "don't lease the IP address to the host with the installed local-administrated bit in address". Sounds interesting, will reconsider this.2 points
-
В файле /opt/etc/init.d/S92syncthing Меняем строку ARGS="" На ARGS="--config=/opt/etc/syncthing/ --data=/opt/root/.local/state/syncthing"2 points
-
Support for use keenetic modem as Tailscale exit node and access home/work network from keenetic modem. Subnet routers and traffic relay nodes · Tailscale Exit Nodes (route all traffic) · Tailscale I currently use raspberry pi as exit node in my network. Here is a client github repository tailscale/tailscale: The easiest, most secure way to use WireGuard and 2FA. (github.com) Tailscale is a VPN that modifies the Wireguard protocol slightly by adding Tailscale discovery messages. Relevant code: https://github.com/tailscale/tailscale/blob/main/disco/disco.go2 points
-
Hello. I think IntelliQoS is missing a few controls. @eralde These are : 1) Enable / disable 2) MBPS / KBPS selection Feature 1 is needed because : SQM cannot be disabled, there is no control for this in the new interface. When you want to disable it, you cannot enter the value 0 or leave it empty. The 2nd feature is needed for the following reason: Sometimes users may want to fine tune the speed in KBPS. I think it would be good to give this choice to the user. https://ibb.co/mBtd1xD2 points
-
Imo it's a must-have feature even for an entry-level router in 2024. I'm using KN-1811. Excellent device. Too bad it just falls flat when it comes to setting up firewall rules overall - too basic, simplistic rules, no flexibility (take for example OpenWRT's firewall). And for IPv6 specifically it simply doesn't exist at all, afaiu. Any plans to introduce it at least via cli?2 points
-
Good afternoon. I propose to enable support in Keenetic routers for connecting UPS power supplies via USB. To be able to monitor and control from Keenetic routers the UPS power supplies unit connected via USB. This is important for remote video surveillance centers connected to the Internet via Keenetic routers. Thanks, Andrej Kuzmin2 points
This leaderboard is set to Moscow/GMT+03:00






.thumb.png.d898712077c24aabbddc2889fcd49996.png)