Leaderboard
Popular Content
Showing content with the highest reputation since 07/31/17 in all areas
-
11 points
-
Hello everyone. Some time ago Adguard offered a "free" alternative like nextdns that "has its own customizable interface". Anyone can use it now, it's in open beta. I think it will have many users as it is a free alternative to NextDns. It would be great if Keenetic brought this new adguard dns as a component. ⬆️ https://adguard-dns.io/en/welcome.html10 points
-
Is it possible to offer dmt dsl drivers with version selection? For example, can options such as 0.46 , 0.47 version be added independently in fw?9 points
-
Hello. There's a custom type of VPN named FortiClient and its open source implementation openfortivpn. It would be great to have a component in Keenetic Web Interface to connect to this type of VPN. Due to there's a source code, it shouldn't be too complicated to implement such feature. Please, create this component as soon as possible Thanks in advance.9 points
-
4.2 is a stable branch, see also changelog 4.1. Supported models: Giga (KN-1010) Hero (KN-1011) Start/Starter (KN-1110, KN-1111, KN-1112) Lite (KN-1310) Omni (KN-1410) City (KN-1510) Air/Explorer (KN-1610, KN-1613) Extra/Carrier (KN-1710, KN-1711, KN-1713) Ultra/Titan (KN-1810, KN-1811) Viva/Skipper (KN-1910, KN-1913) Omni DSL (KN-2011, KN-2012) Extra DSL/Carrier DSL/Skipper DSL (KN-2111, KN-2112) Runner 4G (KN-2210, KN-2211, KN-2212) Hero 4G (KN-2310, KN-2311) Hero DSL (KN-2410) Peak DSL (KN-2510) Giant (KN-2610) Peak (KN-2710) Orbiter Pro (KN-2810) Skipper 4G (KN-2910) Speedster (KN-3010, KN-3012) Buddy 4 (KN-3210, KN-3211) Buddy 5 (KN-3311) Buddy 6 (KN-3411) Voyager Pro (KN-3510) Hopper DSL (KN-3610) Sprinter (KN-3710) Hopper (KN-3810) Explorer 4G (KN-4910)7 points
-
7 points
-
Imo it's a must-have feature even for an entry-level router in 2024. I'm using KN-1811. Excellent device. Too bad it just falls flat when it comes to setting up firewall rules overall - too basic, simplistic rules, no flexibility (take for example OpenWRT's firewall). And for IPv6 specifically it simply doesn't exist at all, afaiu. Any plans to introduce it at least via cli?7 points
-
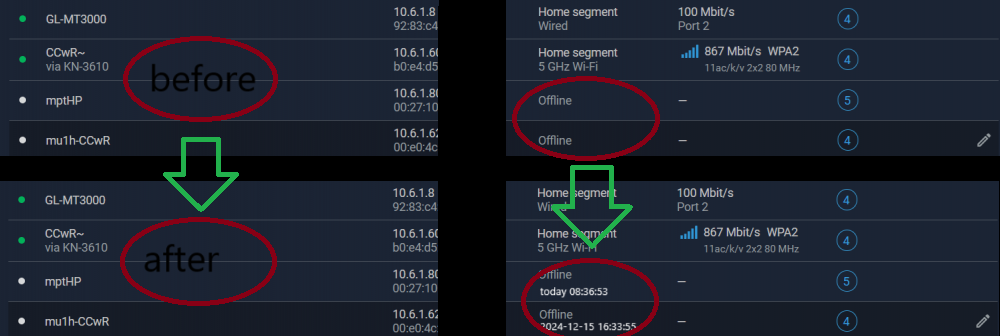
now just says 'offline'.. update that column with "offline/n[datetime]" to see when last-seen... also req#2, Add to devicelist to show recent unregistered clients now offline too -- so over past 24h or past half-dozen over past week... that is just a separate REQ... It surprises me, someone can go onto a Keenetic system a few minutes ago then go offline and be invisible in the UI. I actually prefer a DHCP page where I can see what was recently assigned and so who it was assigned to, but that isn't even fullproof if they go static.6 points
-
Will there be a multilingual user interface option in future plans? I hope there will be a Turkish interface.6 points
-
Make Please NTP server a standard component, without opkg. For devices without / with restricted access to the Internet. Предлагаю сделать NTP-сервер стандартным компонентом, без opkg. Для устройств без доступа/с ограничением доступа к internet.6 points
-
Hello. I think IntelliQoS is missing a few controls. @eralde These are : 1) Enable / disable 2) MBPS / KBPS selection Feature 1 is needed because : SQM cannot be disabled, there is no control for this in the new interface. When you want to disable it, you cannot enter the value 0 or leave it empty. The 2nd feature is needed for the following reason: Sometimes users may want to fine tune the speed in KBPS. I think it would be good to give this choice to the user. https://ibb.co/mBtd1xD6 points
-
Hello, I have recently bought a Keenetic KN-1910 Skipper, but it seems that it lacks RFC4638 support. I set 1500 MTU on the PPPoE connection but a DF ping still shows max MTU of 1492. For RFC4638 support, the ethernet interface would need an MTU of at least 1510 bytes, since it needs to transport packet payload + VLAN tag (802.1q - 2byte) and PPPoE header (6+2=8bytes). My ISP supports RFC4638 and it uses VLAN + PPPoE. Under a different router running OpenWRT, I can set MTU of 1510 and have this working. Would it be possible to add this feature into the next KeeneticOS release, or is there a way to achieve the same permanently (into saved settings) via CLI? Thanks, FC5 points
-
@Pars @PriSonerS61 @ru.celebi @Ahmed Ensar, thank you for your help. The issue is confirmed, it will be fixed in one of the future versions.5 points
-
Release 4.3.0 (preview): Cifs: removed "CIFS" suffix from the mDNS name of the device [NDM-3648] IP: implemented deletion of routes by “route delete” command when importing from a bat-file (reported by @VVS) [NDM-3778] IPv6: implemented DNS server configuration for subnets [NDM-3702]: ipv6 subnet {name} dns-server ({address1} [address2] | disable) Web: fixed absence of buttons on the confirmation popup dialog in the Fail-safe mode (reported by @vk11) [NWI-4143] Web: fixed appearance of the "Read more" button in the list of knowledge base articles (reported by @VVS) [NWI-4137] Web: fixed Applications page loading error [NWI-4104] Web: fixed color of the separation line on the "Network Ports" tile [NWI-4145] Web: fixed excessive row height in the Client Lists table (reported by @AndreBA) [NWI-4133] Web: fixed issues caused by updating the style of control elements (reported by @dimon27254) [NWI-4140] Web: fixed issues in the mobile version of the Connection Policies page (reported by @dimon27254) [NWI-4114] Web: fixed line spacing in text annotations in the mobile version (reported by @dimon27254) [NWI-3872] Web: fixed saving of the main menu in a hidden state when closing and reopening the browser window (reported by @cheburashkaDDNS) [NWI-4120] Web: fixed selection of segments on the traffic monitor pie chart in the mobile version (reported by @dimon27254) [NWI-4079] Web: redesigned "My networks and Wi-Fi" tile on the dashboard [NWI-4071] Wi-Fi: fixed transfer of multicast and broadcast traffic when client isolation is enabled on mt7981-based devices [SYS-1329]5 points
-
So the real feature request sounds as "don't lease the IP address to the host with the installed local-administrated bit in address". Sounds interesting, will reconsider this.5 points
-
Release 4.3 Alpha 12: IPoE: reworked code for configuring Wired connections concerning IPTV, VoIP and VLANs on Ethernet ports [NDM-3586] IPv6: fixed the cause of nginx error “bind() to [fd05:...] failed (Address not available)” [NDM-3525]5 points
-
Dear @AlperShal, As a Product Manager for Keenetic I'd like to inform you that a fix for the aforementioned issues has been planned before this was public and reassure you that we take security very seriously. Due to the very low-risk nature of the reported issue we are going to patch that in our next update, with no urgent-version required for the fix. We feel like explaining the issue is required in this case: The CVE CVE-2024-4022 reported a "leak" of information that is meant to be known. Knowing the Model and the Firmware Version from the Web Interface does not consititute a vulnerability and is intended, so much that we write the Router model name in our UI. For the Firmware version, it is easy to recognize the approximate version due to our constant updates that will, inevitably, modify our front-end pages. The CVE CVE-2024-4021 didn't allow any kind of remote access or control, nor private information leak, they only allowed an attacker to see which components (eg. WPA3-E, WireGuard, OpenVPN) have been installed on the system. This doesn't allow to know if a component is enabled, active or, in case a component is missing from the list, if the service is provided by another device that is not the Keenetic Router (eg. WireGuard may not be installed on the exposed Keenetic Router, but may be provided via Port Forwarding). After consulting with an uninvolved, third-party, Security Researcher, we identified the flaw as a category low, information disclosure. This means that the flaw in itself doesn't compromise anything on the product, but could make some flaws (we are not aware of any flaws that involve our products, as of now) easier to target due to being able to identify if the required components to possibly run the attack are installed on the system, even if the randomness explained before is present. I want to reassure all of our customers that this statement doesn't appear to be correct on our side: the reporter has been in touch with our team and we acknowledged the issue, mentioning that a fix was planned. That said, this confusion during the communications made us understand that we need to improve when dealing with these cases. Starting from today I will start some processes to improve, starting from following RFC 9116, so that everyone that finds a security flaw in our system can go through our responsible-disclosure system and do the right thing. In our complete interest to maintain and keep the trust of all of our loyal customers, I kindly thank you for this post. Dametto Luca, Product Manager for Keenetic5 points
-
Release 4.2 Alpha 2: HTTP: added read/send timeout configuration for proxies [NDM-3157]: ip http proxy {name} timeout {timeout} IPsec: fixed iOS L2TP/IPsec client disconnections under workload [NDM-3180] Web (beta): added missing translations (reported by @dimon27254) [NWI-3361] Web (beta): fixed appearance of HTML code as text (reported by @dimon27254) [NWI-3359] Web (beta): fixed bugs occuring when the "Cloud-based content filtering and ad blocking" component is uninstalled (reported by @dimon27254) [NWI-3360] Web (beta): fixed display of WISP connection details on the dashboard (reported by @dimon27254) [NWI-3339] Web (beta): fixed notifications display in dark theme (reported by @dimon27254) [NWI-3358] Wireguard: added Advanced Security Configuration parameters (requested by @UwU) [NDM-3202]: interface {name} wireguard asc {jc} {jmin} {jmax} {s1} {s2} {h1} {h2} {h3} {h4}5 points
-
Release 4.2 Alpha 1: CLI: implemented "grep" filter for command output [NDM-3075]: command … | grep [-A n] [-B n] [-C n] {pattern} -A — number of lines to show after match -B — number of lines to show before match -C — nesting depth of XML context DNAT: fixed port forwarding issues after Hotspot code refactoring (reported by @flybustier) [NDM-3127, NDM-3171] DNS: fixed CloudFlare filter operation on networks without IPv6 support [NDM-3163] Hotspot: implemented automatic host registration in the Home segment (enabled by default) [NDM-3101]: ip hotspot auto-register disable — disable automatic registration Hotspot: implemented segment-default policy for hosts (enabled by default) [NDM-2237]: ip hotspot host conform HTTP: implemented options to preserve Referer and Origin headers when proxying (reported by @Of Course I Still Love You) [NDM-3089]: ip http proxy {name} preserve-referer ip http proxy {name} preserve-origin IPsec: enabled MOBIKE extension (RFC 4555) for Virtual IP IKEv2 client and server [NDM-3164] NAT: fixed dropping of currently active sessions when "ip static" rules are disabled [NDM-3067] Netflow: implemented support for IPv6 sessions [NDM-3109] NTCE: implemented application filtering [NDM-3069]: ntce filter profile {name} application {application} — add application to the profile ntce filter profile {name} group {group} — add application group to the profile ntce filter profile {name} type {type} — set profile type, which can be “permit” or “deny” ntce filter profile {name} description {description} — set profile description ntce filter profile {name} schedule {schedule} — set profile schedule ntce filter assign host {host} {profile} — assign profile to a registered host (MAC address) ntce filter assign interface {interface} {profile} — assign profile to an interface SIP: implemented filtering of incoming calls [VOX-271]: nvox sip {id} whitelist {digitmap} nvox sip {id} blacklist {digitmap} nvox sip {id} enable-whitelist nvox sip {id} enable-blacklist show nvox sip {id} whitelist show nvox sip {id} blacklist SIP: implemented phonebook support [VOX-326]: nvox phonebook import {filename} {mode} — import contacts in the vCard format filename — *.vcf filename; mode — import mode: replace, overwrite, extend, or duplicate. nvox phonebook delete — delete all contacts from the phonebook nvox sip {id} enable-whitelist-phonebook — enable phonebook as a whitelist filter for incoming calls show nvox phonebook — display all phonebook records VPN: implemented OpenConnect VPN server [NDM-3141]: oc-server interface {interface} — bind OpenConnect server to an interface oc-server pool-range {begin} {size} — set OpenConnect address pool oc-server static-ip {name} {address} — set static IP address for a user oc-server mtu {mtu} — set OpenConnect server MTU oc-server multi-login — enable multiple connections with the same login ip nat oc — enable NAT for OpenConnect clients service oc-server — enable OpenConnect service Web (beta): added a warning about possible connection loss when changing Wi-Fi settings (reported by @dimon27254) [NWI-3249] Web (beta): added links to Extenders on the "Client Lists" page (reported by @dimon27254) [NWI-3189] Web (beta): displayed information about the active sessions count on the dashboard (reported by @dimon27254) [NWI-3326] Web (beta): fixed "Air scanning" dialog on the "Mobile Broadband Internet Connections" page (reported by @dimon27254) [NWI-3193] Web (beta): fixed alignment of input field names (reported by @eda100) [NWI-3239] Web (beta): fixed components list filtering in the System settings (reported by @dimon27254) [NWI-3311] Web (beta): fixed display of "Change Operating Mode" block in the dark theme (reported by @dimon27254) [NWI-3170] Web (beta): fixed display of ACL rules on the Firewall page (reported by @keenet07) [NWI-3153] Web (beta): fixed display of empty band group in "Mobile Broadband Internet Connection" settings (reported by @dimon27254) [NWI-3194] Web (beta): fixed display of a large list of knowledge base articles (reported by @dimon27254) [NWI-3250] Web (beta): fixed display of the chart on the Traffic monitor page (reported by @dimon27254) [NWI-3254] Web (beta): fixed display of wired connections in the MWS table (reported by @dimon27254) [NWI-3214] Web (beta): fixed filters in the MWS transition log (reported by @dimon27254) [NWI-3212] Web (beta): fixed firewall rule editor (reported by @dimon27254) [NWI-3190] Web (beta): fixed header alignment on the login page on mobile devices (reported by @dimon27254) [NWI-3240] Web (beta): fixed minor bugs on the "Mobile Broadband Internet Connections" page (reported by @dimon27254) [NWI-3297] Web (beta): fixed minor issues on the Application traffic analyzer page (reported by @dimon27254) [NWI-3163] Web (beta): fixed saving the Data compression (CCP) checkbox value when PPTP connection is configured (reported by @T@rkus) [NWI-3296] Web (beta): fixed style of select boxes on mobile devices (reported by @dimon27254) [NWI-3192] Web (beta): fixed subnet validation in the firewall rule editor (reported by @dimon27254) [NWI-3213] Web (beta): fixed visibility of Save/Cancel buttons in the System Component Options page (reported by @dimon27254) [NWI-3191] Web (beta): fixed welcome pop-up message on mobile devices (reported by @dimon27254) [NWI-3312] Web (beta): removed text shortening in pop-up dialogs on mobile devices (reported by @dimon27254) [NWI-3181] Web (beta): removed the information "via" which node a device is connected when the "mws" component is not installed (reported by @dimon27254) [NWI-3334] Web (beta): removed the unnecessary horizontal scroll from the block with network ports on mobile devices (reported by @dimon27254) [NWI-3169] Web (beta): updated "Applications" card on the dashboard (reported by @keenet07) [NWI-3188]5 points
-
Good afternoon. I propose to enable support in Keenetic routers for connecting UPS power supplies via USB. To be able to monitor and control from Keenetic routers the UPS power supplies unit connected via USB. This is important for remote video surveillance centers connected to the Internet via Keenetic routers. Thanks, Andrej Kuzmin5 points
-
Asus' high-end devices have a "smart connect rule" mechanism like this. It looks like a detailed version of the "band steering" setting we have. How about applying this to keenetic? https://ibb.co/12xNpHt5 points
-
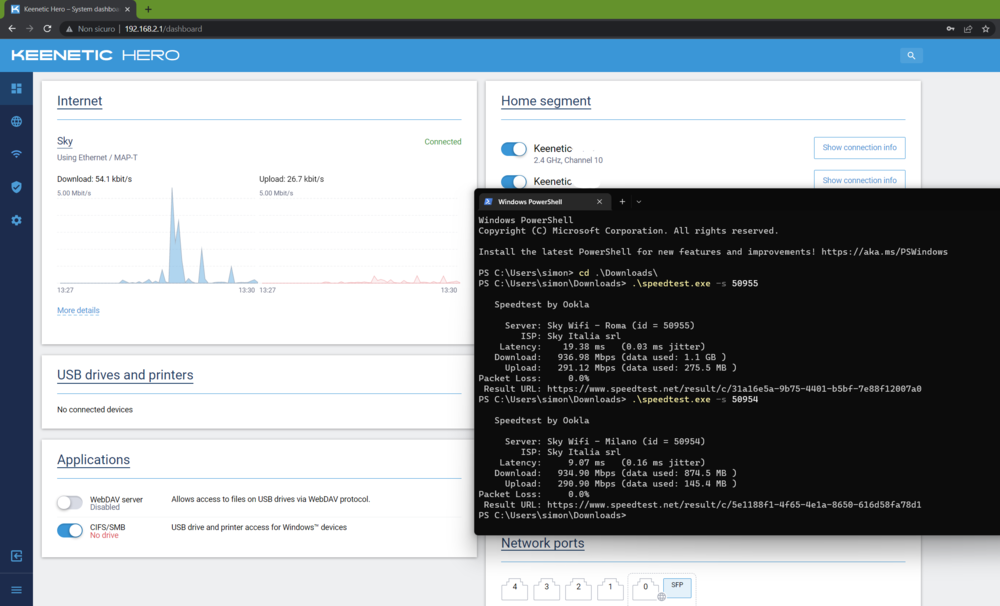
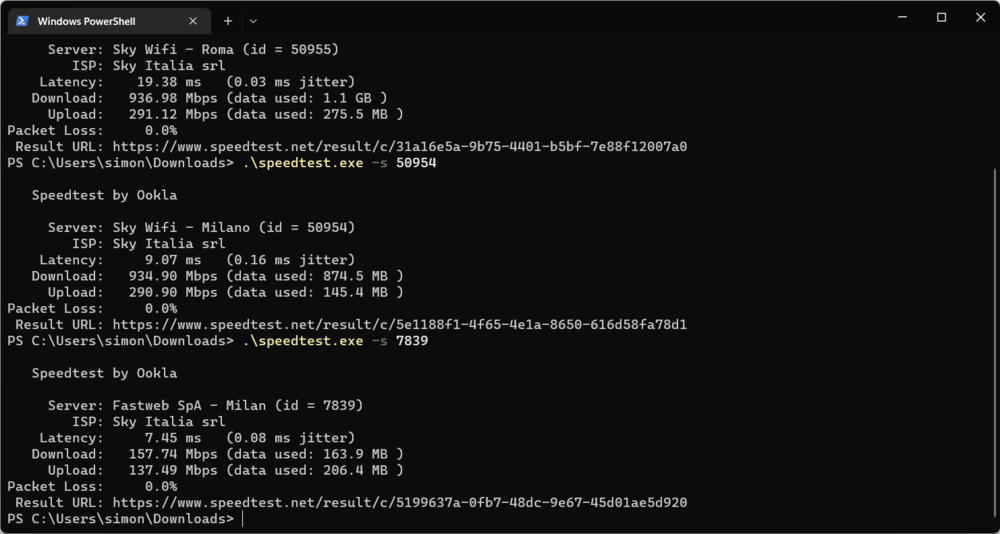
FTTH 1000/300 Mbps Sky MAP-T with Keenetic HERO AX Honestly, I am incredulous of the performance (in IPv4 with offloading), I am used to seeing poor results on most of the hardware I have seen/tested. I want to congratulate all the Keenetic staff who did a great job. In particular a raspberry pi only works with a customised image made by a forum.fibra.click user that modifies the load balancing management between the cpu's for a moment and requires a specific NIC tp link. Despite this, very good performance is only achieved in IPv6, a speedtest server in IPv4 witout offloading gives results in line with or worse than other devices with OpenWrt, but with offloading the performance are good!. In any case, the values eventually settle at very similar devices such as the belkin ax3200 with a very similar hw. 3.8.5 (no offloading) 3.9 Beta 1 (offloading) Then we come to the MTU side, which has never been written about on this forum but I imagine the engineers who have worked on it know: MAP-T requires an extra 20 bytes of MTU per packet in IPv4, there are two solutions: increase the IPv6 MTU to 1520 decrease the IPv4 MTU to 1480 If not handled correctly this causes problems on sites such as atm.it, ebay. All of these sites do, so again I congratulate the person who made this implementation. What's more, it works the site that never worked in the openwrt implementation of MAP-T www1.sky.com/opensourcesoftware/ As you can see from speedguide.net/analyzer.php it is reduced to 1480 because MTUs above 1500 are not supported, the other option would also be convenient. what is missing from this implementation? implementation of the possibility of requesting an IPv6 prefix (sky leaves the possibility of requesting a prefix that you have already obtained via ia_pd), this was implemented by a user of the forum.fibre.click on openwrt, the patch can be found here https://github.com/edofullin/odhcp6c Jumbo Frame to allow you to have a MTU > 1500 and thus not have to have a 1480 MTU in IPv4. (the OP tells me it is possible via CLI, as soon as I have some time I will test it) Better IPv4 performance, performance in IPv6 is very good (I hope that improving the hw/sw offloading will bring about the canonical 930 Mbps in IPv4).5 points
-
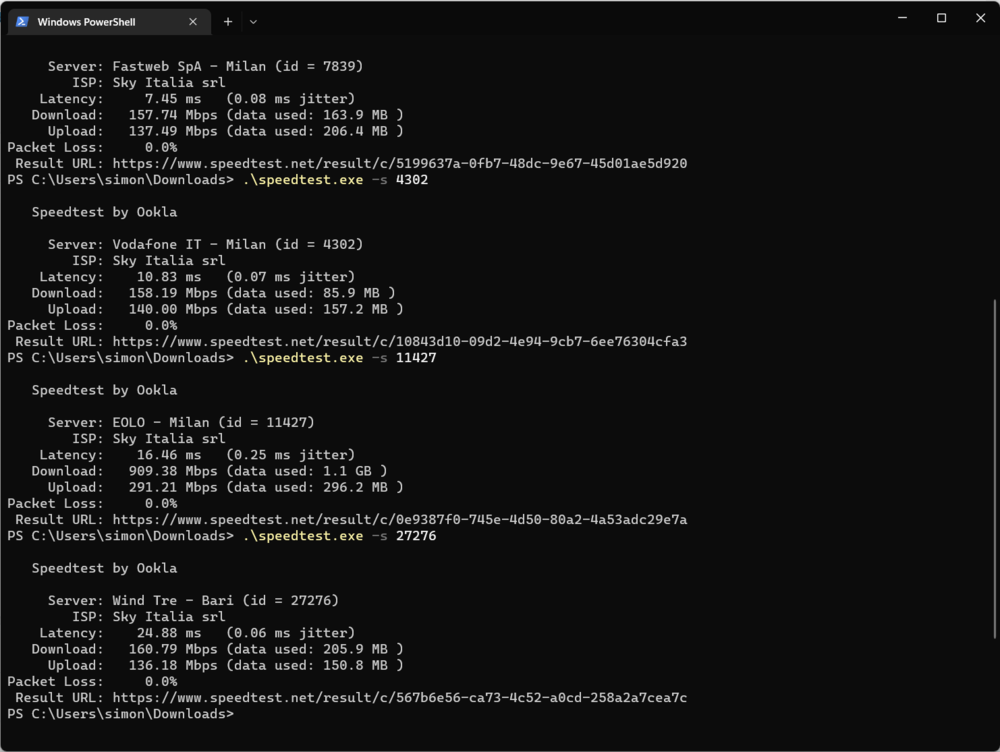
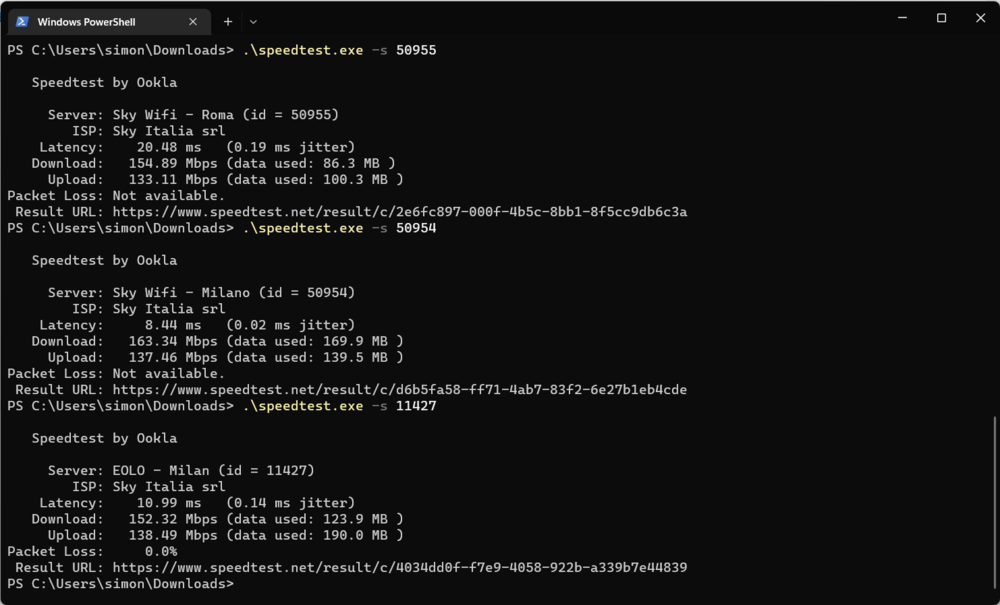
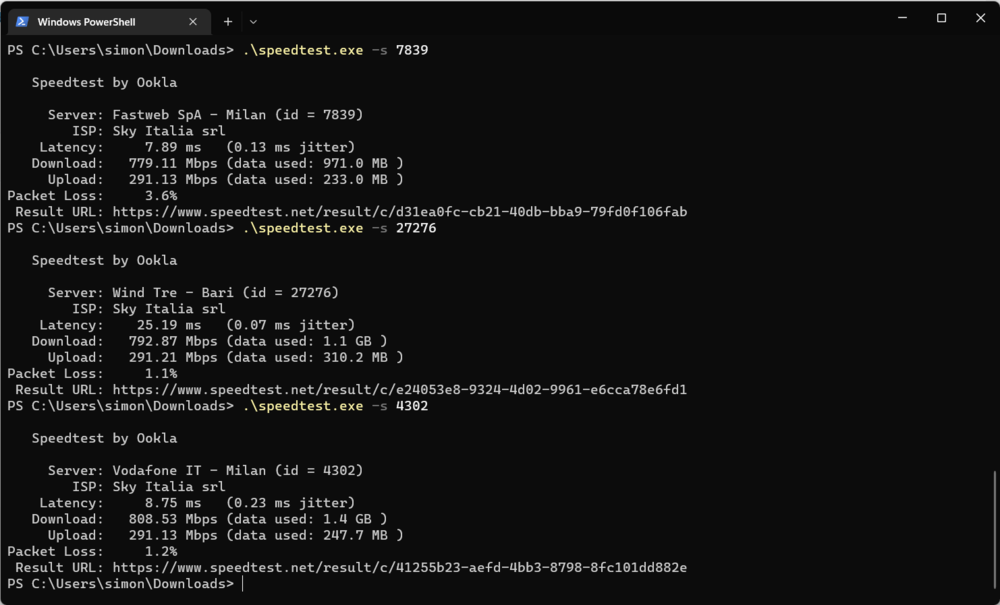
Hi, In some cases it is necessary to measure the connection performance between the Keenetic device and the ISP. However the results of speed testing applications, like fast.com, nperf etc., which runs on the computer, are bound to the quality of wi-fi connections or the performance of operation system itself. Thus, the results may not be project the connection quality between the ISP and the Keenetic device. I tried the iperf3 package to measure the speed between the ISP and the Keenetic , but I couldn't connect to none of the public servers. It would be great if there is a speedtesting application on KeeneticOS, with a user friendly UI, 1- Which measures the speed between the keenetic device and the ISP (a software that runs directly on the keenetic device like iperf3). 2- Which measures the connection performance between the home networkind device (pc, mobile phone etc.) and the keenetic device. The seperated results helps us to detect at which point the connection performance issues occur. Kind regards Gökalp5 points
-
[UPDATE] New mechanism for working with devices! Dear users, we've successfully completed switching to a new mechanism for working with devices. We recommend supporting KeeneticOS 3.7 and higher The KeeneticOS version for adding new devices is 3.6.3 and higher [still]5 points
-
5 points
-
Updates December 16, 2021: Beta 3.0 Release: [NEW] Keenetic OS version update for network controllers [NEW] Reboot controllers [NEW] Batch operations for update and reboot [NEW] Tasks page Improvements: CIR-1636 // Removed scroll lock after closing PopUp menu CIR-1592 // Fixed a bug with underlining the header tab in Location after authorization CIR-1673 // Fixed highlighting of the "Hosts" icon on the "Devices" page5 points
-
Hello, I need auto wake on lan client with specific date and time also one time or every day, every week, every month, every year like windows task scheduler. Can you add this next future uptade KeeneticOS 4.3 ? There are many Keenetic devices and PCs in our network. This feature is very necessary for our it department. Thanks, Kind regards.4 points
-
Today the French mobile operator Free/Iliad, launched its fiber offering in Italy, similar to Sky for the lack of IPv4 the Iliad fiber uses MAP-E and a 4in6 tunnel (rfc2473). In France it uses since 2015 in non-densely populated areas a version of MAP-E a moment acerbic apparently from French forums, also often referred to as 4rd (although it has nothing to do with RFC 7600), as configuration from DHCPv6 does not seem possible. The operator offers very high speeds in terms of Gbps, despite this in areas where the deployment of ftth is older offers the classic speed of 1Gbps. A keenetic router as long as it works well could be a good solution for cities where there is the maximum limit of 1Gbps (like Milan, Turin and Bologna, 3 of the most important cities in Italy). From the guides for the free router it seems that it is possible to configure IPv4 even without MAP-E support, most likely it is part of a separate pool to offer IP 1:1 to those who request it, through a 4in6 tunnel (rfc2473). If the router supports MAP-E in Italy, at least from the first information it seems that it can be configured by DHCPv6 (unlike in France). From early February we will know more information about IPv4 share ratio and other details about MAP-E, like if it uses many disjointed ranges like Sky or few contiguous ranges like in France. I wanted to know if along with MAP-T development there is MAP-E development, and if keenetic support 4in6 tunnels (rfc2473). If I am not mistaken MAP-E is also used in Japan with a share of 1:256.4 points
-
Release 4.3.2 (preview): DNS: fixed behavior of an empty DNS profile [NDM-3843] IPoE: fixed IP address loss on the Home segment when setting port 1 as WAN on KN-3910 [NDM-3830] IPsec: fixed access to the bound network segment for L2TP/IPsec VPN clients [NDM-3715] OpenConnect: fixed compatibility with VPN Client Pro for Android (reported by @Mechanics) [NDM-3838] Opkg: fixed running single commands via "ndmc" (reported by @spatiumstas) [NDM-3837] USB: added support for Fibocom FM190W modem [NDM-3849] Web: fixed various bugs in the interface (reported by @spatiumstas, @dimon27254, @iggo) [NWI-4214]: NWI-4178, NWI-4013, NWI-4187, NWI-4194, NWI-4196, NWI-4197, NWI-4004 Wi-Fi: fixed wireless client disconnection by timeout on AX3000 access points [SYS-1337] ZeroTier: fixed identity.public validation for big-endian (mips) devices (reported by @gaaronk) [NDM-3821]4 points
-
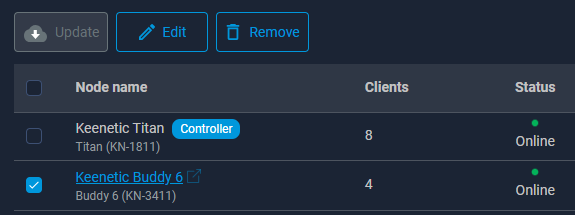
Please consider adding a "Reboot" button next to the existing Edit and Remove buttons in the mesh device management interface. Currently, restarting a mesh node requires logging into each device separately, which is inefficient and time-consuming. Suggested Placement: [Update] [Edit] [Remove] [Reboot] This addition would make it much easier to manage and restart mesh nodes directly from the controller interface.4 points
-
Release 4.3 Beta 2 (preview): DNS: implemented subdomain resolution in "object-group fqdn" (reported by @avn) [NDM-3726] HTTP: fixed Cookie handling and related "Core::Scgi::Tools: bad request: no session" error during authorization (reported by @snark) [NDM-3713] HTTP: fixed missing static DNS records when "ip http proxy dns-override" is enabled (reported by @Leshiyart) [NDM-3718] IPv6: fixed 6in4 tunnel performance when hardware packet engine is enabled [SYS-1271] OpenSSL: updated to 3.3.3 [SYS-1306] Proxy: fixed resetting of interface counters when it is shut down (reported by @keenet07) [NDM-3724] SFP: fixed KN-1012 compatibility with RTL9601D-based SFP modules [SYS-1313] Web: fixed redundant warning about unsaved changes during firmware upgrade (reported by @dimon27254) [NWI-3944] Web: fixed showing a scroll-bar when dragging objects in the connection priority list (reported by @dimon27254) [NWI-4044] Web: fixed showing an alert about unset password when it's already set (reported by @dimon27254) [NWI-4033] Web: fixed status showing not inserted SIM card on the dashboard (reported by @spatiumstas) [NWI-4016] Web: fixed tooltip readability in the Application Traffic Analyser table (reported by @dimon27254) [NWI-4020] Web: fixed unexpected second reboot after a system update (reported by @spatiumstas) [NWI-4047] Web: fixed Wi-Fi network shutdown despite canceling this action in a pop-up dialog box (reported by @dimon27254) [NWI-4010] Web: improved appearance of the side menu [NWI-3839] Web: locked the LTE signal metrics button when no connection is established (reported by @spatiumstas) [NWI-4015] Web: redesigned password input field with indication of password strength [NWI-4030]4 points
-
Release 4.3 Beta 1 (preview): Dns: implemented object groups with automatic FQDN name resolution [NDM-3692]: object-group fqdn {name} — create an FQDN object group object-group fqdn {name} include {address} — add an address to the group Opkg: added a hidden command to display the system name of a network interface (requested by @Ponywka) [NDM-3694]: show interface {name} system-name Storage: fixed mounting HFS+ volumes larger than 6TB [SYS-1143] Web: fixed background color of "show threads" output in Web CLI (reported by @spatiumstas) [NWI-4052] Web: fixed display of manually configured HTTPS port in KeenDNS links (reported by @bigpu) [NWI-4027] Web: fixed Fast Transition (802.11r) reset to Disabled when changing SSID on one band [NWI-3900] Web: fixed text description for OpkgLedControlX handler (reported by @dimon27254) [NWI-3997] Web: implemented a setting that allows to assign a specified home network segment to the Extender's Ethernet port [NWI-3571] Web: locked configuration-related system settings when the fail-safe mode is active [NWI-4032] Web: updated modal window behavior and layout [NWI-3979]4 points
-
Release 4.3 Beta 0.1: DNS: fixed forwarding of transit queries allowed in the system profile [NDM-3651] DNS: fixed initialization of DoT/DoH when static DNS servers are configured for unused connections (reported by @Robespierre) [NDM-3681] MWS: fixed wireless backhaul reconnection when WPA3 is enabled [SYS-1281] OpenVPN: fixed resolving remote endpoint using A (IPv4) DNS queries when IPv6 is running [NDM-3640] Proxy: increased the maximum number of Proxy interfaces to 64 [NDM-3686] SFP: implemented SFP+ and combo port operation mode settings [NDM-3181]: interface {name} media-type {type} — set combo port media type: auto — prefer SFP with auto-failover to MDI (default) mdi — enforce media type to MDI sfp — enforce media type to SFP interface {name} sfp pcs {mode} — set Physical Coding Sublayer (PCS) mode: auto — autodetect from DDMI(default) fallback — sequentially try fixed baseband modes until one of them works sgmii/an — SGMII-supported speeds of 10/100/1000 Mbps with auto-negotiation enabled 1000base-x/an — fixed 1 Gbps baseband with Clause 37 auto-negotiation enabled 1000base-x — fixed 1 Gbps baseband 2500base-x/an — fixed 2.5 Gbps baseband with Clause 37 auto-negotiation enabled 2500base-x — fixed 2.5 Gbps baseband interface {name} sfp rx-los {mode} — set SFP RX_LOS reception mode: auto — autodetect from DDMI (default) accept — accept RX_LOS signal ignore — ignore RX_LOS signal interface {name} sfp init-timeout (auto | {timeout}) — set SFP module initialization timeout in seconds Storage: enabled UASP support for external USB drives [SYS-1290] USB: added support for Sierra MC7304 modem [NDM-3684] Web: fixed auto-completion for "no" with arguments in Web CLI (reported by @dimon27254) [NWI-4022] Web: fixed refreshing of active connections uptime on the dashboard (reported by @k19olegh68) [NWI-4034] Web: fixed unsaved changes warning on Mobile Broadband Internet Connections page (reported by @spatiumstas) [NWI-3999] Web: improved handling of continued commands in Web CLI (reported by @TopGear78) [NWI-3738]4 points
-
Release 4.3 Alpha 14: Ethernet: fixed 100 Mbps link on a 2.5 Gbps port [SYS-1275] Kernel: fixed system clock drift on mt7981-based devices (reported by @dimon27254) [SYS-1273] OpenVPN: updated to 2.6.13 [NDM-3660] SSTP: fixed "session-preempt" configuration [NDM-3662] Web: fixed appearance of "-1" in Application traffic analyzer (reported by @dimon27254) [NWI-4008] Web: fixed issues on Mesh Wi-Fi system page (reported by @dimon27254) [NWI-4002] Web: fixed update channel tooltip on the dashboard (reported by @dimon27254) [NWI-3932]4 points
-
The main idea is to add the ability to reject connections based on MAC address patterns (masks) in cases where white/blacklists are not flexible enough for configuration.4 points
-
Release 4.3 Alpha 13: AFP: enabled Time Machine attribute for all shares by default [NDM-3510]: afp share {label} {mount} [timemachine] [{description}] IPoE: fixed "voip" role assignment (reported by @Leshiyart) [NDM-3643] IPv6: fixed 6in4 tunneling when static MTU is set [NDM-3644] Web: fixed display of connection name in the “Signal Levels” pop-up (reported by @dimon27254) [NWI-3978] Web: fixed errors in log when adding a DNS server (reported by @dimon27254) [NWI-3991] Web: fixed traffic monitor card on the dashboard (reported by @spatiumstas) [NWI-3921]4 points
-
Release 4.3 Alpha 1: DHCP: implemented configuration of interface-specific relay agents [NDM-3401]: interface {name} ip dhcp relay enable — enable DHCP relay on an interface interface {name} ip dhcp relay upstream server {address} — specify an upstream DHCP server interface {name} ip dhcp relay upstream interface {interface} — bind DHCP upstream to a specific interface (optional) HTTP: implemented "connect" method to allow for OpenVPN proxying [NDM-3497]: ip http proxy {name} upstream (http | https | connect) {upstream} [port] IP: added settings for policy-specific routes [NDM-3435]: ip policy {name} route ( {network} {mask} | {host} ) ( {gateway} [interface] | {interface}) [auto] [metric] [reject] ip policy {name} ipv6 route {prefix} ( {interface} [gateway] | {gateway} ) [auto] [metric] [reject] IP: implemented protection against connection table overflow [NDM-3362]: ip conntrack max-entries {max-entries} — set conntrack table size ip conntrack lockout disable — disable conntrack table protection (enabled by default) ip conntrack lockout threshold public {public} — set maximum number of connections from public interfaces (percentage of the conntrack table size, from 50 to 99, default value: 80) ip conntrack lockout duration {duration} — set lockout duration in seconds (from 60 to 3600, default value: 600) ip conntrack sweep threshold {threshold} — set threshold to start cleaning up waiting sessions (percentage of the conntrack table size, from 50 to 99, default value: 70) show ip conntrack lockout — view lockout status IPsec: fixed KeenDNS access to device via IKEv2 connection [NDM-3439] MWS: fixed host uptime reset when roaming between access points (reported by @Radyohead) [NDM-3498] Opkg: disabled restarting of initrc when changing "dns-override" configuration (reported by @Zeleza) [NDM-3496] Proxy: increased maximum identity length from 64 to 128 characters [NDM-3512] SFP: added quirks for GPON modules on KN-1012 [SYS-1209]: ODI DFP-34G-2C2 ODI DFP-34X-2C2 ODI DFP-34X-2C3 Torrent: implemented setting for background priority of disk I/O (reported by @Andrey812) [NDM-3436]: torrent io-priority low USB: added support for ZTE MU5001 5G modem [NDM-3500] VPN: added ability to preempt VPN sessions when multilogin option is disabled (reported by @krasnoperovrv) [NDM-3450]: crypto map {name} l2tp-server session-preempt VPN: fixed dropping of active connections to the server when user account settings are changed [NDM-234] Web: added IPv6 settings for VPN Connections [NWI-3428] Web: added display of extra access points included in segments (reported by @Leshiyart) [NWI-3743] Web: added timer for on-demand mode in WISP settings [NWI-3570] Web: changed colors on traffic monitor charts (reported by @KYTECHNGAMING) [NWI-3699] Web: fixed USB Devices display when unmounting all partitions (reported by @spatiumstas) [NWI-3762] Web: fixed color of "System mode" radiobuttons (reported by @dimon27254) [NWI-3714] Web: fixed header of policy configuration at Connection Policies page (reported by @Gonzik) [NWI-3781]4 points
-
Release 4.2.0 (preview)*: Torrent: fixed sudden crash and restart of “transmission” service [NDM-3477] * released for devices with USB storage support.4 points
-
Release 4.2 Alpha 11: Core: fixed "ppe" settings format (reported by @keenet07) [NDM-3311] DNS: fixed reset of static IP settings after device reboot [NDM-3303] DNS: improved robustness of the DoT/DoH cache [NDM-3320] DynDNS: fixed validation of domain names (reported by @Михаил Касванд) [NDM-3309] Mobile: fixed "interface mobile pdp" setting (reported by @k19olegh68) [NDM-3312] OpenSSL: switched to 3.0.13 [SYS-1152] VLAN: implemented mapping of NTCE priority to 802.1p PCP for egress packets (reported by @Gim12) [NDM-3318]: interface {name} vlan qos egress map {priority} {pcp} priority — NTCE priority queue number. If the value is 0, all outgoing packets will receive the given PCP; pcp — 802.1p PCP value. Web (beta): improved behavior of toggles in tables (reported by @keenet07) [NWI-3465] Wi-Fi: fixed 5 GHz channel width degradation on Buddy 6 [SYS-1151] ZeroTier: added support for DNS and global routes (reported by @drno88) [NDM-3319]4 points
-
Release 4.2 Alpha 10: Core: fixed inversion of certain boolean settings (reported by @dimon27254) [NDM-3297] Core: fixed returning "null" for undefined boolean settings (reported by @agentOleg) [NDM-3298] OpenVPN: fixed spurious reconnects of OpenVPN client [NDM-3301] SNMP: fixed ifAdminStatus monitoring for Ethernet ports [NDM-3296] USB: fixed "interface usb apn" setting (reported by @Grigoriy) [NDM-3307] VPN: implemented adherence to the policy of the bound interface [NDM-3295] Web (beta): added OpenConnect to the Applications page [NWI-3407] Web (beta): fixed "Server address" input validation for OpenConnect (reported by @snark) [NWI-3463] Web (beta): fixed display of connections that use IPv4 over IPv6 [NWI-3472] Web (beta): fixed display of the backup peer address for IPsec connections (reported by @feoser) [NWI-3464]4 points
-
Hi, sorry for that, we've had a deployment issue on the weekend, so it didn't go out for some devices. We are fixing it right now.4 points
-
This restriction will be removed. NDM-30394 points
-
That's a mistakenly late-activated protection rule, previously intended to protect users from installation of Alpha 12. It is supposed to be active until at least tomorrow. The mechanism of these rules still clearly needs to be further developed for such cases. We apologize for the inconvenience.4 points
-
Hello, I would like to report a few bugs I noticed. @eralde @Anna Zhelankina 1) When the logo is clicked to return to the homepage (/dashboard) from a different page in the mobile view, it redirects to the /dasboard page, but the menu is automatically open. It should be closed. It works properly in the old interface, the new interface has a problem in this way. 2) The "command line" option that appears in the desktop version does not appear in the mobile view. 3) When the "Traffic monitor" page is opened for the first time, the time interval in the graph is nested. It will be fixed if the time interval is changed. This issue is triggered only when the "Traffic monitor" page is opened for the first time. 4) When I want to list the interfaces in the "default route" on the "Routing" page, I get a strange error. The "save" and "cancel" buttons are located above the interface names. (The z-index value for the row with the buttons is set to 70, so they are always at the top. Changing the value to 1 fixes problem 4 and 5) 5) In the same way, when I want to list the interfaces in a setup with a "default route", the scroll does not work in the interfaces section and there is a huge gap. If you reduce the height of the page and force the menu to open upwards, the "interfaces" are displayed properly. 6) The warning text that appears in Turkish in the "my network and wifi" section on the home page is in English. It should be in Turkish. There is also a difference between the English text that appears when Turkish is selected and the English text that appears when English is selected, even though they mean the same thing. 7) Although Turkish language is selected, the segment names on the "Wireless Access Control" page are in English. 8) The Turkish equivalent of "Import settings from previous router" is a bit long, so it does not fit in the allocated space and overflows.4 points
-
The interface is lacking some critic iPv6 configuration options and information boxes. Client iPv6 addresses in the client list and/or client information box > more information. Ability to set static iPv6 address to a client if possible. (I am not sure if this makes any sense or is applicable but while my server is using SLAAC address constantly others are not and they are changing every once in a while. So it would be nice to have the option to statically set it for those we need. (Not a networking expert so not sure if the ip is being given by the router or requested by the client)) Ability to add iPv6 static routes from web interface as an alternative to `ipv6 static [protocol] [interface] [mac] [port]` command. Ability to add iPv6 firewall rules from the web interface. (Related to previous entry) Ability to set router iPv6 address from web interface as an alternative to `interface [interface] ipv6 address [ipv6]4 points
-
The Internet is a door that allows us to open up to the world. I am a person who believes that I will do this with Keenetic in the past and today, as well as in the future, without any problems. I'm going to talk about a modular USB device that has never been sold in the EU and TR. Zyxel Keenetic Plus DSL. I cannot use the device on Keenetics with EU and TR regions. The device may not be suitable for marketing after the change of the brand name and with the advancement of technology, and/or its production may have stopped, or a new device may be considered instead. Despite this, it is still sold in the RU market both in local locations and available at shop.keenetic.ru, and it does not appear to be sold out on Keenetic.ru, like the Keenetic City model. https://keenetic.ru/ru/keenetic-city Universally, I or anyone else can still access/own this device. There is also a compatibility list on the relevant market and promotion pages of the product. (By the way, the list on the shop side is not up to date.) https://keenetic.ru/ru/zyxel-keenetic-plus-dsl https://shop.keenetic.ru/product/zyxel-keenetic-plus-dsl https://keenetic.ru/storage/uploads/certificates/98288150-39de-4cb8-bf45-93b69c0e4a14.pdf In the product introduction, it is written that it may be compatible with the new Keenetic router models with a USB port, apart from the models with built-in DSL feature. But nowhere is "COMPATIBILITY AVAILABLE ONLY FOR DEVICES SOLD IN RU MARKET" and/or "DOES NOT WORK IN SPECIFIC REGIONS". such information was not specified and could not be found. --------------------------------------------- --------------------------------------------- In this case, when I am curious and maybe want to experience this product for a long time; I have to make the following inferences. 1- To request the removal of this restriction for a modular product 2- I want the region of my current Keenetic device to be changeable. 3- Aiming to buy a new Keenetic router with RU variant. 4- Removing and/or destroying the device. I live in Antalya, Turkey. Maybe many people will know that Antalya is one of the provinces that received the most immigration due to the war. I also formed very good friendships with a friend I met through the Keenetic group. While I was trying to help them, they also brought me various gifts out of my Keenetic love. I thank him very much. @Jattiko He also uses his beloved Keenetic in our country. And with my recommendation, Zyxel Keenetic PLUS DSL, it has a smooth internet experience. Likewise, while he can use the USB module with the RU variant device, I cannot use it within the same province. As EU, TR and RU users, I'm curious about your thoughts on my thinking. pls comment!!4 points
-
Updates July 5, 2022 New: Added new events for notifications in Telegram: change statuses on the device (member) device was rebooted (via RMM) network was rebooted (via RMM) device was updated (only for controllers, via RMM) Added an Uptime filter to the Devices page Improvements: Added the ability to save page pagination - now you can choose once how many rows of networks / devices to display on the page and when you re-enter this setting will already be saved; topic Split the ‘Address’ column into ‘IPv4’ and ‘MAC address’ for Devices and Hosts; Added the possibility that when an error occurs and the page is reloaded, you remain on the same page that you were before; Fixed the order of statuses in the filter on the Networks and Devices pages - now the order is the same as on the Dashboard; Other interface improvements4 points
-
Updates May 18, 2022: New functionality: [NEW] New side menu and navigation Note: profile, 2f. auth and dark mode have moved to the Settings4 points
-
Hello Keentic, for usage in e.g. a company it would be good to have a Landing Page for WLAN to accept Terms of use for guests. Right now there is no feature like this, so I would like to request it. Regards Benjamin4 points
-
4 points
This leaderboard is set to Moscow/GMT+03:00