Leaderboard
Popular Content
Showing content with the highest reputation since 02/07/26 in all areas
-
5.1 is an experimental branch, see also changelog 5.0. Supported models: Giga (KN-1010) Hero (KN-1011, KN-1012) Start/Starter (KN-1111, KN-1112, KN-1121) Air/Explorer (KN-1613, KN-1621) Extra/Carrier (KN-1711, KN-1713, KN-1714, KN-1721) Ultra/Titan (KN-1810, KN-1811, KN-1812) Viva/Skipper (KN-1910, KN-1912, KN-1913) Omni DSL (KN-2011, KN-2012) Extra DSL/Carrier DSL/Skipper/Speedster DSL (KN-2111, KN-2112, KN-2113) Runner 4G (KN-2210, KN-2211, KN-2212, KN-2213) Hero 4G (KN-2310, KN-2311) Hopper 4G+ (KN-2312) Hero DSL (KN-2410) Peak DSL (KN-2510) Giant (KN-2610) Peak (KN-2710) Orbiter Pro (KN-2810) Skipper 4G (KN-2910) Speedster 4G (KN-2911) Speedster (KN-3010, KN-3012, KN-3013) Buddy 4 (KN-3210, KN-3211) Buddy 5 (KN-3310, KN-3311) Buddy 5S (KN-3410) Buddy 6 (KN-3411) Voyager Pro (KN-3510) Hopper DSL (KN-3610, KN-3611) Sprinter (KN-3710, KN-3711) Sprinter SE (KN-3712) Hopper (KN-3810, KN-3811) Hopper SE (KN-3812) Challenger (KN-3910) Challenger SE (KN-3911) Racer (KN-4010) Buddy 6 SE (KN-4410) Explorer 4G (KN-4910) Orbiter 6 (KAP-630)3 points
-
Release 5.1 Alpha 3 DynDNS: fixed the 'URL must be filled for custom type' error preventing operation with custom servers (reported by @snark) [NDM-4292] Web: implemented turning off the modem power cycle for custom Internet availability checker modes [NWI-4629] Web: improved the port forwarding rule management buttons for the mobile view of the registered client settings (reported by @dimon27254) [NWI-4672] Web: corrected the sorting of clients by IP address in the client lists (reported by @dimon27254) [NWI-4677] Wireguard: added support for advanced ASC parameters via configuration file import or by using CLI (requested by @FLK) [NDM-4298] interface {name} wireguard asc {jc} {jmin} {jmax} {s1} {s2} {h1} {h2} {h3} {h4} [{s3} {s4} {i1} {i2} {i3} {i4} {i5}] Known issues: System update operation on devices with NAND memory is partially blocked. Please visit Download Center for your model and use the Recovery Utility to restore, or upload an image from our KeeneticOS archive via tftp.3 points
-
Release 5.1 Alpha 4 Core: fixed the 'nand_do_write_ops: attempt to write non page aligned data' error preventing system update operation (reported by @Aleksey Mikhaylov) [NDM-4307]2 points
-
Release 5.0.7 (previewstable): DynDNS: added the DuckDNS preset [NDM-4273] Hotspot: implemented commands to turn off the SSDP and WS-Discovery network host discovery methods [NDM-4283] interface {name} ssdp disable interface {name} wsd disable HTTP: enhanced the process for renewing the SSL certificate for the system domain name [NDM-4284] LTE: implemented a timeout mechanism to switch back to the primary SIM on the dual-SIM modem [NDM-4129] interface {name} suspend timeout {seconds} interface {name} suspend schedule {schedule} MWS: fixed the issue with the connection display for wired client devices [NDM-4282] Web: implemented turning off the modem power cycle for custom Internet availability checker modes [NWI-4629] Web: added support for IPv6 URIs when configuring DNS-over-TLS (DoT) and DNS-over-HTTPS (DoH) secure DNS servers [NWI-4610] Web: improved toggle state indication [NWI-4661] Web: fixed the shortening of client names (reported by @dimon27254) [NWI-4668] Web: fixed the sorting mode icon display in content filter settings (reported by @dimon27254) [NWI-4671] Web: fixed the actuation of toggles for the mobile view (reported by @spatiumstas) [NWI-4632] Web: fixed the tooltip display in proxy connections list (reported by @spatiumstas) [NWI-4670] Web: improved the line wrapping for the mobile view of the system log (reported by @spatiumstas) [NWI-4680] Wi-Fi: resolved the issue of the channel width decreasing below 80 MHz when the Adjustment ZeroWait DFS is active [SYS-1544] Wi-Fi: eliminated security vulnerabilities [SYS-1542] CVE-2014-3570 CVE-2022-43042 points
-
Release 5.1 Alpha 2 Hotspot: implemented commands to turn off the SSDP and WS-Discovery network host discovery methods [NDM-4283] interface {name} ssdp disable interface {name} wsd disable HTTP: enhanced the process for renewing the SSL certificate for the system domain name [NDM-4284] LTE: implemented a timeout mechanism to switch back to the primary SIM on the dual-SIM modem [NDM-4129] interface {name} suspend timeout {seconds} interface {name} suspend schedule {schedule} MWS: fixed the issue with the connection display for wired client devices [NDM-4282] Storage: improved operation with USB drives that report abnormal 'discard' capabilities [NDM-4291] Web: implemented turning off the modem power cycle for custom Internet availability checker modes [NWI-4629] Web: fixed the sorting mode icon display in content filter settings (reported by @dimon27254) [NWI-4671] Web: fixed the tooltip display in proxy connections list (reported by @spatiumstas) [NWI-4670] Web: improved the line wrapping for the mobile view of the system log (reported by @spatiumstas) [NWI-4680] Wi-Fi: resolved an issue where the ZeroWait DFS adjustment prevents the use of selected Wi-Fi channel width [SYS-1544] Wi-Fi: eliminated security vulnerabilities [SYS-1542] CVE-2014-3570 CVE-2022-43042 points
-
I’ve been using KeenDNS for years without any problems. However, for the past few hours, I haven’t been able to access my router via my KeenDNS domain. Is anyone else experiencing the same issue today?2 points
-
Hello everyone. Some time ago Adguard offered a "free" alternative like nextdns that "has its own customizable interface". Anyone can use it now, it's in open beta. I think it will have many users as it is a free alternative to NextDns. It would be great if Keenetic brought this new adguard dns as a component. ⬆️ https://adguard-dns.io/en/welcome.html2 points
-
Release 5.1 Alpha 1 Dns: implemented basic access authentication (RFC 7617) for DNS-over-HTTPS (DoH) server URIs [NDM-4168] DynDNS: added the DuckDNS preset [NDM-4273] IPv6: implemented IPv6 access lists [NDM-4130] ipv6 access-list {acl} ipv6 access-list {acl} (permit | deny) ((tcp | udp) ({source} | (host {source}) | any) [port (((lt | gt | eq) {source-port}) | (range {source-port} {source-end-port}))] ({destination} | (host {destination}) | any) [port (((lt | gt | eq) {destination-port}) | (range {destination-port} {destination-end-port}))]) | ((((ipv6 | esp | ahp | pcp | sctp)) | {protocol}) ({source} | (host {source}) | any) ({destination} | (host {destination}) | any)) | (icmp ({source} | (host {source}) | any) ({destination} | (host {destination}) | any) [(icmp-message | ({icmp-type} [{icmp-code}]))]) ipv6 access-list {acl} rule {index} (disable | (schedule {schedule}) | (order {new-index}) | (description {description})) ipv6 access-list {acl} auto-delete KeenDNS: fixed updating static DNS records after switching the service from cloud to direct mode [NDM-4255] Storage: implemented tools to check and format the file system [NDM-4239] media {name} partition {partition} check media {name} partition {partition} format {type} Web: added IPv6 rule configuration to firewall [NWI-4614] Web: dedicated a page for configuring storage devices and USB devices [NWI-4583] Web: added support for IPv6 URIs when configuring DNS-over-TLS (DoT) and DNS-over-HTTPS (DoH) secure DNS servers [NWI-4610] Web: fixed editing of DNS-based routing rules (reported by @dchusovitin) [NWI-4622] Web: fixed the actuation of toggles for the mobile view (reported by @spatiumstas) [NWI-4632] Web: fixed the shortening of client names (reported by @dimon27254) [NWI-4668] Web: improved toggle state indication [NWI-4661] Web: implemented reordering of DNS-based routing rules [NWI-4659] Wi-Fi: fixed the cause of Wi-Fi clients dropping from 80 MHz channel width when the Adjustment ZeroWait DFS was triggered [SYS-1544] ZeroTier: implemented an option to connect to custom networks that use private root servers (moons) [NDM-4236] interface {name} zerotier orbit {world-id} {moon-id}2 points
-
Release 5.0.6 (preview): Ethernet: restored the cable diagnostics functionality for 2.5 Gbit/s ports [SYS-1529] HTTP: eliminated CVE-2026-1642 security vulnerability in the HTTP proxy service [NDM-4267] KeenDNS: fixed the inaccessibility of domain name to clients on the home network after switching the service from cloud to direct mode [NDM-4255] LTE: fixed the mobile data packet loss when polling the SMS subsystem of the built-in modem [NDM-4244] LTE: fixed the improper dual-SIM slot switching operation with the ping-check enabled (reported by @Ста По) [NDM-4237] MWS: fixed the cause of the 'response is too big' error message logged by the Wi-Fi System controller [NDM-4250] MWS: improved the Wi-fi System extender discovery to employ both L2 (LLDP) and L3 (multicast WS-Discovery) protocols and support specific configurations of managed Ethernet switches [NDM-4220] Web: fixed the radio button operation for selecting the Wi-Fi bands in the client settings (reported by @dimon27254) [NWI-4630] Web: corrected the display of wired clients connecting through Wi-Fi System extenders (reported by @Gonzik) [NWI-4667] Web: fixed the Wi-Fi System transition log filtering by client names that contain spaces (reported by @dimon27254) [NWI-4616] Wi-Fi: fixed the cause of Wi-Fi clients dropping from 80 MHz channel width when the Adjustment ZeroWait DFS was triggered [SYS-1544] Wi-Fi: resolved rejection of Wi-Fi clients trying to associate with 'IE_SUPP_CHANNELS' request element exceeding 64 bytes [SYS-1539]2 points
-
Hello @eralde The problem is still occurring.1 point
-
Vorrei suggerire l'implementazione di una funzionalità software per migliorare la stabilità e la gestione del Wi-Fi a 5GHz, simile a quanto già presente in apparati professionali (come Ubiquiti per esempio). Attualmente, quando la selezione del canale 5GHz è impostata su "Auto", i router Keenetic scansionano l'intero spettro, includendo e preferendo da come vedo i canali DFS (52-144), soprattutto quelli superiori al 100. Sebbene questi canali offrano più larghezza di banda, a volte la frequenza viene disattivata troppe volte. Il router è costretto a interrompere le trasmissioni per 10 o 1 minuto (come da manuale) a seconda se è canale 100 e superiore o 52 e superiore, causando instabilità. Al momento, l'unica soluzione per l'utente è bloccare manualmente un canale specifico (36, 40, 44 o 48), perdendo però i vantaggi della selezione automatica in caso di interferenze. Soluzione proposta: Aggiungere un semplice interruttore (Toggle) nelle impostazioni Wi-Fi 5GHz: "Consenti l'uso dei canali DFS" (Sì/No). Se impostato su SÌ (default): Il router continua a funzionare come ora, scegliendo tra tutti i canali disponibili. Se impostato su NO: L'algoritmo di selezione automatica viene limitato esclusivamente ai canali non-DFS (dal 36 al 48).1 point
-
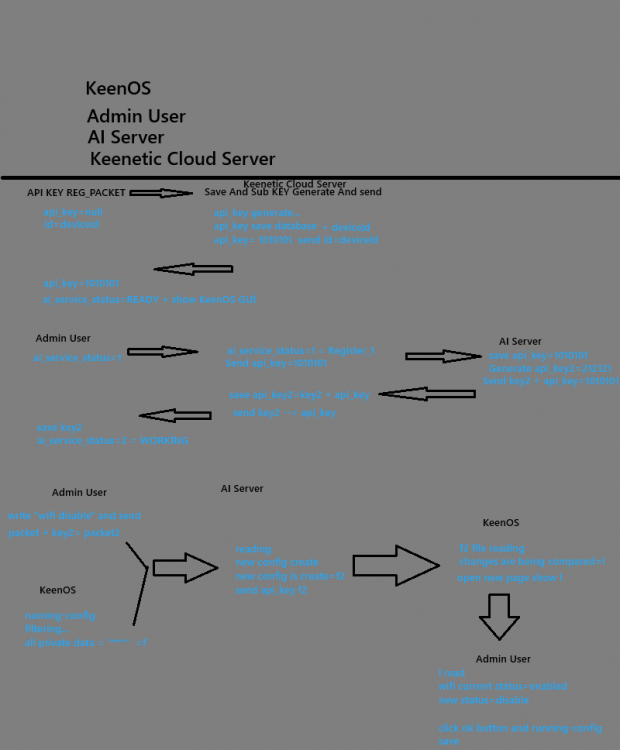
-Google Translate: Hello, I recently received help from AI while troubleshooting some issues with my router, and it was very helpful. I had an idea about how to integrate this into the system, and I'd like to share this model with you. Adding such a feature would be beneficial. The visual is roughly prepared to help understand the logic. It could be a similar model.1 point
-
The main thing is that everyone is silent, no one who is knowledgeable will write an explanation. It seems that the developers only read the Russian forum.1 point
-
In the Command Reference Guide, you can read about call filtering features implemented in KeeneticOS. Pay attention to the commands specified below. nvox sip blacklist nvox sip whitelist nvox phonebook import nvox sip enable-blacklist nvox sip enable-whitelist nvox sip enable-whitelist-phonebook show nvox blacklist show nvox whitelist show nvox phonebook show nvox sip-lines1 point
-
That really depends on the applications you want to use there. If you plan to use a BitTorrent client to download smth., then you may need more storage than available on an average USB thumb drive. In this particular case, an external SSD would be the best choice, but the maximum read/write speed will be limited by the USB port (SSDs are usually faster). You can transfer your existing OPKG configuration to the new drive. I don't have any personal experience with this, but I've seen reviews from people who have done it.1 point
-
@Jim, installing OPKG (the base system + all the packages you choose) on an external USB drive is the assumed default setup. It definitely works.1 point
-
You should also be able do delete everything created by the OPKG installer via the web UI/telnet.1 point
-
Hello, I need auto wake on lan client with specific date and time also one time or every day, every week, every month, every year like windows task scheduler. Can you add this next future uptade KeeneticOS 4.3 ? There are many Keenetic devices and PCs in our network. This feature is very necessary for our it department. Thanks, Kind regards.1 point
-
Hello, Jim 🙂 Nothing is wrong with trying OPKG if you want to configure something that is not possible with the stock firmware. That being said there is no official support for any OPKG-related issues, so if you have an issue you will have to refer to other users, e.g., here on the forum or in the OpenWRT community. However, since Keenetic firmware is not OpenWRT the advice you will get from the OpenWRT community may be not fully applicable. On the other hand, I would suggest that you just back up your router's firmware and configuration files (startup-config) once you configured the stock firmware the way you want it. You can do that via the web UI. Even if something goes wrong with the OPKG, you can go the the router's web UI, de-select the USB drive you've installed OPKG to and keep using the stock firmware until you want to try again. If the "something goes wrong" situation is worse and you can't access the web UI -- you will always be able to restore the stock firmware using the files you backed up *. * The startup configuration file does not contain encryption keys used in the Wi-Fi system or in WireGuard interfaces. That means that if you restore your router's configuration using a backed up startup-config file, you will have to re-acquire any Wi-Fi system extenders (if you have them) and re-create WireGuard interfaces (if you use them).1 point
-
Dear community, If I have two keenetic routers, the second one used as an extender, and two providers' cables, is the following possible? ISP1 - Keenetic1 - Keenetic2 - ISP21 point
-
Hi, Jim! I am not sure I can answer all of your questions completely, but I will try to do my best: 1 + 2. If you are talking about RAM, then you can monitor that parameter in the web UI dashboard. There is no general rule of thumb on how many different service you will be able to run at the same time, so it is trial and error. If you meant permanent storage, than I would recommend to install the open package system on a USB drive. There is an option to install it on the device internal storage, but the available space will be quite limited. 3. You can check this GitHub repo and this section of the forum (the Entware Quickstart thread is a good start 🙂) 4. After setting up Entware/OPKG and logging into the SSH shell it provides, you can run opkg update && opkg list to see all the packages available for your device: 5. You can leave the "initrc script" field empty, the installer will fill this parameter automatically. Out KB article on how to install Entware on your router: https://help.keenetic.com/hc/en-us/articles/360021214160-Installing-the-Entware-repository-package-system-on-a-USB-drive1 point
-
I am a PS5 Pro owner, and despite the console supporting wifi 7 and MLO, I am experiencing significant connection issues when trying to connect to my Titan 1812 router. Here are the specific problems: AX/BE 5ghz band issues: The device fails to connect to the 5 ghz band (AX or BE). it consistently defaults to 2.4 ghz. I have tried adjusting the band steering to favor 5 ghz and even forced the device to only use 5 ghzz, but in those cases, it refuses to connect entirely. Low speeds on 2.4 ghz BE: It does connect via 2.4 ghz BE, but the speeds are capped around 50-60 Mbps, even though the Titan is positioned very close to the PS5. MLO failure: After establishing a 2.4 ghz connection, whenever I enable MLO in the PS5 settings, the connection drops completely. I suspect this is an issue related to the Titan router, as I have tested this with another Playstation device and encountered the same results. Are there any other PS5 Pro and Titan 1812 users experiencing similar issues? Thanks.1 point
-
Support for use keenetic modem as Tailscale exit node and access home/work network from keenetic modem. Subnet routers and traffic relay nodes · Tailscale Exit Nodes (route all traffic) · Tailscale I currently use raspberry pi as exit node in my network. Here is a client github repository tailscale/tailscale: The easiest, most secure way to use WireGuard and 2FA. (github.com) Tailscale is a VPN that modifies the Wireguard protocol slightly by adding Tailscale discovery messages. Relevant code: https://github.com/tailscale/tailscale/blob/main/disco/disco.go1 point
-
Good afternoon. I propose to enable support in Keenetic routers for connecting UPS power supplies via USB. To be able to monitor and control from Keenetic routers the UPS power supplies unit connected via USB. This is important for remote video surveillance centers connected to the Internet via Keenetic routers. Thanks, Andrej Kuzmin1 point
This leaderboard is set to Moscow/GMT+03:00